Welcome to the Intruvent Edge!
New Home, New Look
Hello readers and happy Friday! You may notice that this newsletter looks quite a bit different than previous versions. That's because we have a new home! We are now publishing the newsletter on Substack. This platform allows us to deliver higher quality content to you, our audience. If you ever want to check on previous issues or to see some of our other posts, you can bookmark the site at: https://edge.intruvent.com.
What We’ve Been Building
NOVA Reaches 1.0 Stability! Our AI-powered threat translation engine, NOVA, has hit a major milestone. NOVA transforms complex threat intelligence into executive-ready insights, making cybersecurity risks understandable for non-technical decision makers.
BRACE Platform Progress: We've made significant strides with our predictive threat defense platform. We are about 80% done with the 1.0 production system and hope to finish this month. Our back end database is operational and we are hosting an enterprise-grade application platform in Azure. While we work on 1.0, Our MVP is live and generating reports by vertical, complete with MITRE ATT&CK mapping and actionable remediation steps. If you know anyone that would like to participate in the free Pilot program, send an email to pilot@intruvent.com.
LATEST NEWS:
The Salesloft Drift Supply Chain Attack (see Deep Dive below for more details) While others are still figuring out what happened, we've been tracking and mapping the UNC[six]395 threat actor's tactics in BRACE. This wasn't just another breach… it shined a light into one of the major weaknesses in cybersecurity: supply chain risk. By stealing access “keys” from trusted third-parties, attackers can bypass your entire security stack. We've already built detection rules and response procedures for our clients. Want a threat actor playbook for UNC[six]395?* Send an email with “TA Playbook” in the subject to contact@intruvent.com and we’ll send you the report (for free).
MS-ISAC Funding Crisis With DHS pulling $27M in funding, 19,000 local governments are about to lose critical threat intelligence. We're stepping up to help. If you know organizations affected by this shutdown, send them our way at contact@intruvent.com - we're working on special programs to fill this gap.
*Attack group purposely “defanged” to prevent searches on our newsletter platform
The DEEP DIVE: The Salesloft Drift Supply Chain Attack
When most people think of a cyberattack, they picture a hacker hammering away at our firewalls trying to brute-force their way in. That’s the Hollywood version. The reality is that attackers have figured out an easier path: they go after the contractors and service providers we’ve already invited into the house.
Think about how your home works. You might give a trusted contractor a set of keys so they can repair your roof while you’re at work. If someone copies those keys without your knowledge, that outsider can walk right in—no need to break a window or set off an alarm. In the digital world, those “keys” are the tokens, passwords, and integration hooks we give our vendors so their software can connect to ours. That’s what we mean by a supply chain attack: the attacker doesn’t target us directly; they compromise one of our suppliers, steal their access, and ride it straight into our environment.
The recent Salesloft-Drift breach is a textbook example of a supply chain attack. Salesloft, which had acquired Drift last year, provides sales engagement tools that plug directly into customer relationship management platforms like Salesforce, email services like Google Workspace, and even cloud platforms like Amazon Web Services (AWS). To make those integrations seamless, companies hand over special digital tokens (essentially copies of the keys to the house) so the tools can work without constant logins. Attackers stole those tokens. Once in hand, they didn’t need to guess passwords or break through defenses; they simply impersonated legitimate connections and moved data out quietly. More than 700 organizations were affected, including some of the most security-conscious firms in the world.
Why does this matter to us? First, it scales. One compromise at a vendor can ripple across hundreds of customers in days. Second, it bypasses traditional defenses. Because these connections are trusted, most security tools treat them as friendly traffic and don’t raise alarms. And third, it hits the business where it hurts. Sales, finance, HR—all of them rely on Software as a Service (SaaS) vendors. If those vendors are compromised, companies feel it in operations, customer trust, and potentially revenue.
Now, what can we do about it? In the short term, Google wrote up a great article on the attack, and is getting the word out. All of the major players (Google, Amazon, Microsoft, etc) have revoked old tokens and reviewed which vendors actually need access. For the house analogy that we used above it’s like checking who still has a spare key and making sure former contractors can’t get in.
Supply chain attacks are increasing almost exponentially. Why? Here’s how you can think about it: cybercriminals are no longer trying to break in at the front door. They’re going after the plumbers, electricians, and contractors who already have access. It’s the reality of modern business, where every digital service is both a convenience and a potential risk. Our as job as security professionals isn’t to eliminate those risks entirely… that’s impossible. But we can manage them, limit the blast radius when things go wrong, and hold vendors accountable for protecting the trust we extend to them.
Supply chain attacks aren’t a rare anomaly anymore. They’re part of the cost of doing business in an interconnected world. But with vigilance, tighter vendor management, and clear accountability, we can reduce the risk and keep those borrowed keys from being misused. There are entire companies out there that specialize in minimizing supply chain risk. Our friends at Netrise (Netrise.io) are doing a great job at dissecting and flagging risky software from suppliers. I highly recommend checking them out.
Technical Deep Dive: UNC[six]395
For cybersecurity professionals, here’s the technical analysis portion of our newsletter. (If you want a full Threat Actor Playbook, including IOCs and Threat Hunting queries, email us at contact@intruvent.com.)
Here's a quick rundown from BRACE about some of the Threat Actor’s key characteristics:
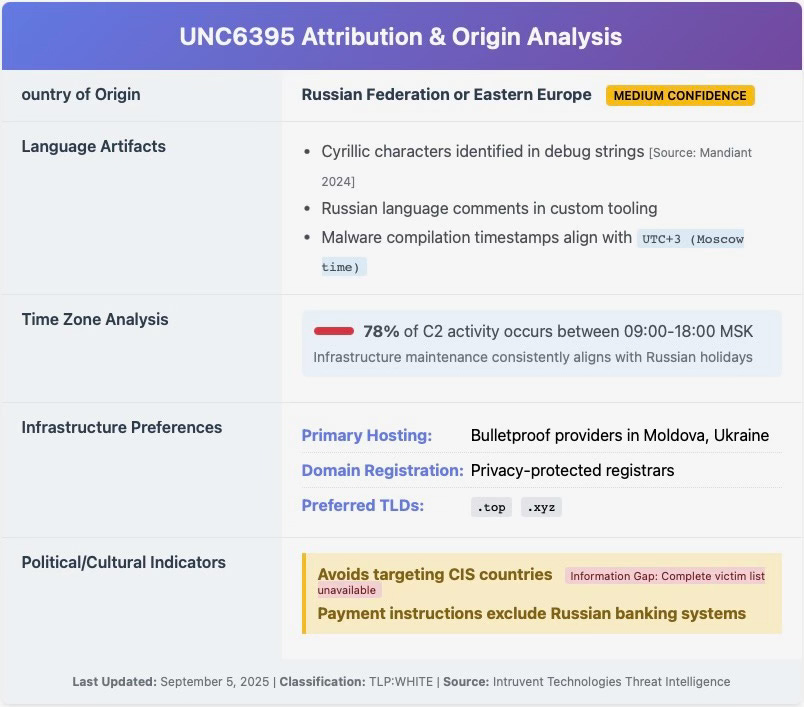
They are an advanced group with fairly high technical skills. We know that they are Russian speaking and have been active since 2022. They also avoid targeting countries that are in the former Soviet Union.
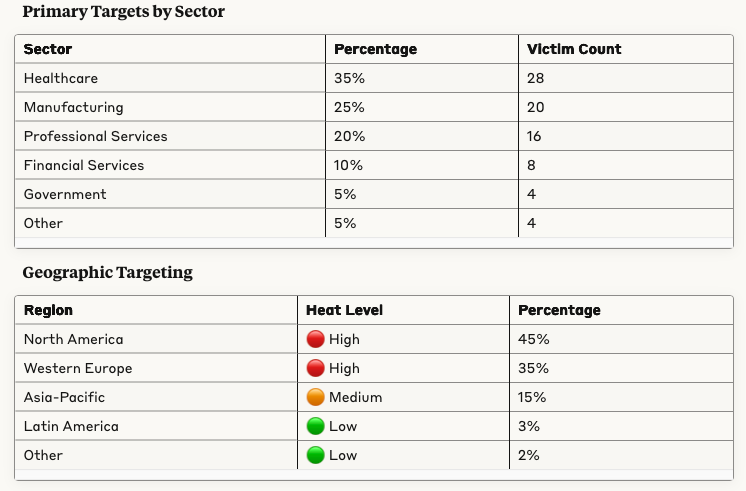
We did a thorough analysis of their victims and have identified the following statistics:
TARGETING ANALYSIS
Victim Selection Criteria:
Annual revenue >$50M USD
(some victims) Limited cybersecurity maturity
Reliance on legacy systems
High-value intellectual property
Cyber insurance coverage confirmed
Evolution Over Time: Initial focus on opportunistic targets has evolved to deliberate selection based on financial capacity and likelihood of payment. Increasing focus on healthcare sector noted since Q3 2024.
CURRENT/MOST RECENT CAMPAIGN DEEP DIVE
Campaign: "Dark Winter"
Timeframe: 2025-01-20 to Present
Objectives: Financial extortion through ransomware deployment
Targets: North American healthcare and critical infrastructure
Attack Chain Analysis:
Initial Access:
Exploitation of unpatched Citrix Gateway appliances (CVE-2023-4966)
Phishing campaigns with healthcare-themed lures
Purchase of access from initial access brokers
Exploitation:
Leverages ProxyNotShell vulnerabilities in Exchange servers
Exploits unpatched VMware vCenter instances
Abuses legitimate remote access tools (TeamViewer, AnyDesk)
Privilege Escalation:
PrintNightmare exploitation (CVE-2021-34527)
Zerologon attacks where applicable
Token impersonation via legitimate tools
Lateral Movement:
RDP with compromised credentials
PsExec for remote execution
WMI for stealthy movement
Cobalt Strike beacon deployment
Exfiltration:
Rclone to cloud storage providers
Custom exfiltration tool "DataMule"
Staged compression using 7-Zip
C2 Infrastructure:
Primary: HTTPS beaconing to compromised WordPress sites
Secondary: DNS tunneling via custom protocol
Tertiary: Telegram API for notifications
Technical Analysis:
Malware Families:
NightCrawler v3.2 (custom ransomware)
ShadowLoader (custom loader)
Cobalt Strike 4.9.1 (cracked version)
SystemBC (proxy/backdoor)
Custom Tools Developed:
DataMule: High-speed exfiltration utility
CryptoLocker2025: Ransomware variant with ChaCha20 encryption
ShadowWipe: Anti-forensic tool
LOTL Usage:
PowerShell for reconnaissance and execution
WMI for persistence and lateral movement
Living off legitimate admin tools (PsExec, RDP)
Native Windows utilities for defense evasion
Persistence Mechanisms:
Scheduled tasks masquerading as Windows updates
Service creation with benign names
Registry autostart entries
WMI event subscriptions
Recommended Mitigations:
Here are some actions that your organization can take to defend against attacks from this threat actor:
Immediate (24-48 hrs): [Priority: Critical]
Cycle any external OAuth tokens
Block identified IOCs at perimeter security devices
Reset credentials for privileged accounts
Disable unnecessary PowerShell usage for standard users
Implement application whitelisting for script execution
Enable enhanced PowerShell logging
Short-term (1-2 weeks): [Priority: High]
Deploy EDR to all critical systems
Implement network segmentation for critical assets
Review and harden RDP configurations
Conduct vulnerability assessment and patching
Implement MFA for all remote access
Long-term (Strategic): [Priority: Medium]
Develop and test incident response playbooks
Implement Zero Trust architecture
Deploy deception technologies
Establish threat hunting program
Regular tabletop exercises
Thank you!
Thank you for continuing to be a reader of our newsletter. We are constantly striving to make these newsletter more useful to you. If you have any suggestions, please let us know at contact@intruvent.com
If you'd like to join the brace pilot program and receive our vertical deep dives as well as our threat actor playbook please email us at pilot@intruvent.com.
If you'd like the entire threat actor playbook for the actor that we reviewed above, please email us at contact@intruvent.com with the subject of their email TA playbook.
And most importantly, if you like the newsletter and you think somebody else would find it useful, please forward this to them so that they could subscribe and get these delivered. Thanks!