The Intruvent Edge: The Supply Chain Bomb
Supply chain attacks doubled this year... and that was before the mega supply chain breach that dropped yesterday
Each month Intruvent releases reports detailing the cyber threats facing each of the CISA-identified Critical Infrastructure Sectors (Nuclear, Financial, Healthcare, etc). I was excited to talk about our September reports today. There are some eye-opening findings in them…. But in the last 24 hours a massive story has rocked the cybersecurity industry:
Seattle-based firewall vendor F5 released a statement yesterday on their website detailing a long-term breach by an advanced, nation-state actor which Reuters is reporting to be a Chinese Advanced Persistent Threat (APT) actor. From the disclosure:
“In August 2025, we learned a highly sophisticated nation-state threat actor maintained long-term, persistent access to, and downloaded files from, certain F5 systems. These systems included our BIG-IP product development environment and engineering knowledge management platforms. We have taken extensive actions to contain the threat actor. Since beginning these activities, we have not seen any new unauthorized activity, and we believe our containment efforts have been successful…. We have confirmed that the threat actor exfiltrated files from our BIG-IP product development environment and engineering knowledge management platforms. These files contained some of our BIG-IP source code and information about undisclosed vulnerabilities we were working on in BIG-IP.”
Ohhhh boy.
F5 is a well respected vendor whose products are widely used by Fortune-500 companies and Governments around the world.
This means that an advanced threat actor had long term access to their product development environment, downloaded the source-code for their software and extracted vulnerability information.
Think of it like this: F5 makes the digital locks protecting Fortune 500 companies and governments around the world. A threat actor didn’t pick those locks…they broke into F5’s factory where the locks are designed and manufactured. They stole the engineering specifications for how every lock works and the quality control reports listing which lock models have defects that haven’t been fixed yet.
That threat actor now has a comprehensive understanding of every weakness in systems protecting some of the world’s most sensitive networks.
So just how bad is this? Here is a look at the potential scope:
Actual Scale:
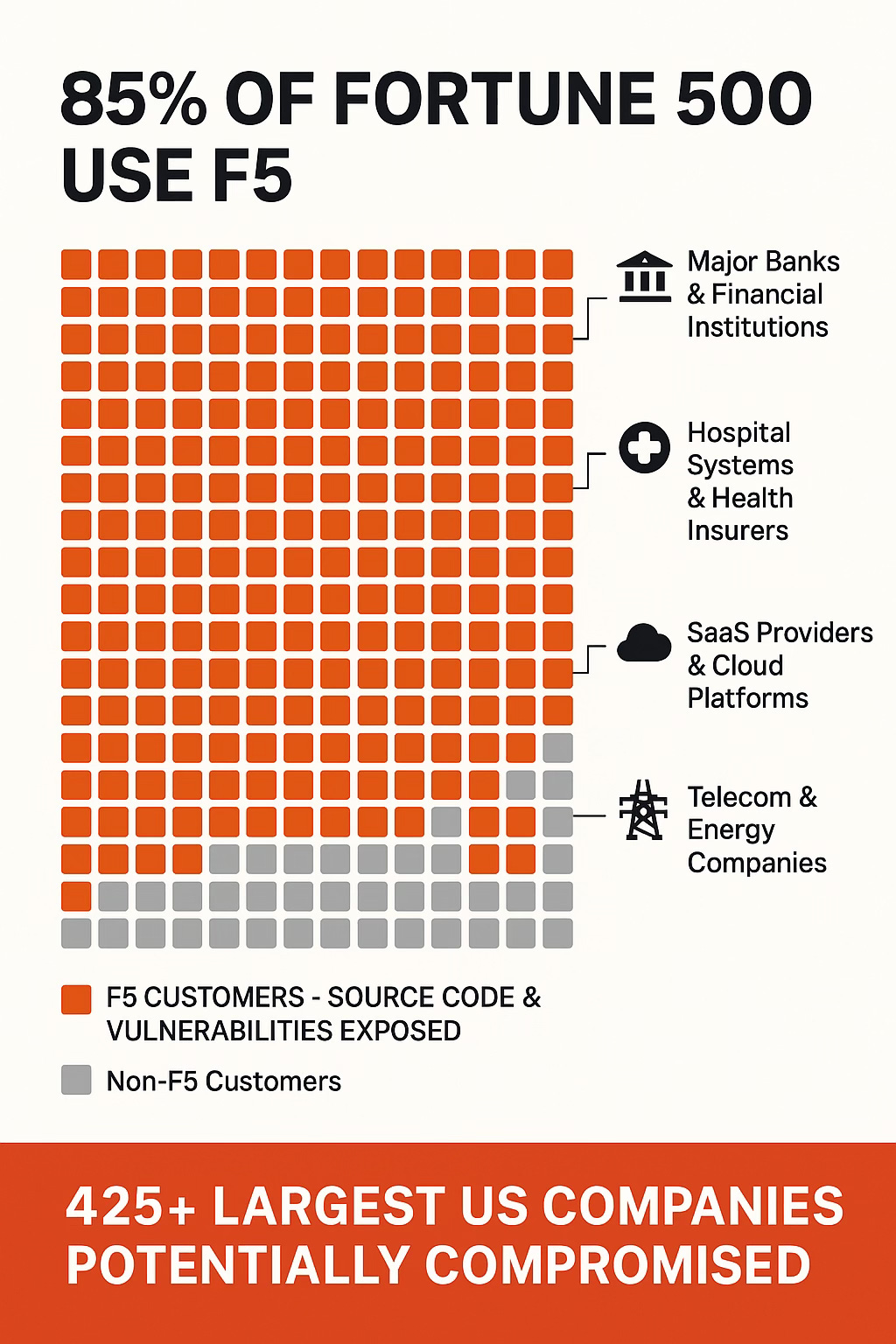
Over 85% of Fortune 500 companies are F5 customers (that’s 425+ of the largest companies in the US) [TechCrunch, October 2025]
1,000+ corporate customers officially [TechCrunch, October 2025]
61,000+ companies use F5 BIG-IP Platform globally [Datanyze market intelligence]
Top 10 mobile service providers (by revenue) all use F5 [F5 corporate materials]
8 of top 9 SaaS providers are F5 customers [F5 corporate materials]
We’re looking at potential impact to 60,000+ organizations including the majority of Fortune 500 companies, major banks, critical infrastructure, and government agencies.
So this is big. VERY BIG.
And this is a supply chain breach. We will delve into this in the next section [Supply Chain: The Math that Changed Everything], but we are potentially looking at downstream compromises as well. [Editor’s note: according to F5, no downstream compromises have been reported yet.].
Let me pause and be clear here. F5 is the Victim in this scenario. They are a good company that is facing one of the hardest situations that any company can face. We’ll do a PSA in the Deep Dive and share investigation and containment guidance from Government agencies around the world. But suffice to say that this is a big breach that will be felt for a long time.
Shifting gears, Let’s look at a few of the headlines from the September BRACE reports, and due to the F5 coverage, we will delve into more September report data in the next edition of Intruvent EDGE.
Three developments this month that are changing how we need to think about cyber defense.
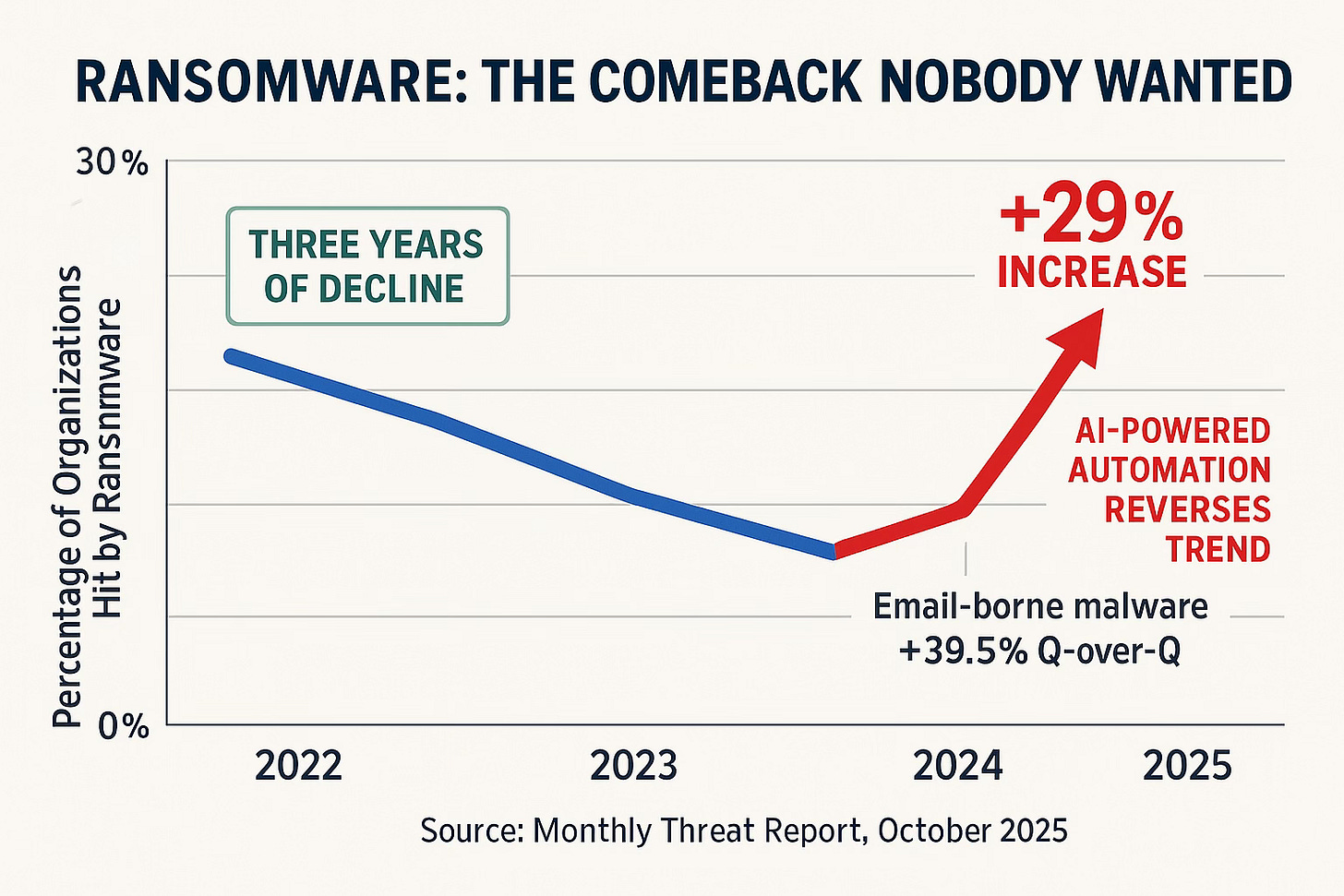
First: Ransomware Made a Violent Comeback
After three years of declining numbers, ransomware reversed course hard. 24% of organizations got hit this year versus 18.6% last year. [1] The driver: AI-powered automation that scales attacks faster than defenders can respond. Email-borne malware spiked 39.5% quarter-over-quarter, with AI-generated phishing content so sophisticated that traditional indicators (grammatical errors, awkward phrasing) have essentially disappeared.
Attackers are now using ICS calendar files as social engineering delivery vectors. That meeting invite from your “vendor”? It might be malware. The quality improvement in AI-generated content means your users can’t spot the difference anymore.
Second: The Bybit Heist Set a New Standard for Audacity
New reports on February 2025’s Bybit attack show that it is the largest cryptocurrency theft in history. North Korea’s Lazarus Group compromised Bybit’s cold wallet transfer process using malicious JavaScript injection during what appeared to be routine operations. The haul: $1.5 billion in Ethereum. They laundered $160 million in the first 48 hours alone. [2]
This was patient reconnaissance, sophisticated tradecraft, and operational security that would make most intelligence agencies jealous. Cold wallets are supposed to be the Fort Knox of crypto storage… air-gapped, offline, protected. Lazarus found a way in anyway through the human/technical interface where even the most secure systems become vulnerable.
Third: The Legal Framework for Threat Intelligence Sharing Just Vanished
The Cybersecurity Information Sharing Act (CISA) expired October 1st during the government shutdown. This is the law that enabled private-sector to government threat intelligence sharing with legal liability protections. Without it, we’re operating in legal uncertainty right when coordination matters most. [3]
Organizations are now questioning: Can we share indicators with federal partners? With industry peers? What’s our liability exposure? The lapse creates uncertainty precisely when we need faster information sharing to counter accelerating threats.
Supply Chain: The Math That Changed Everything
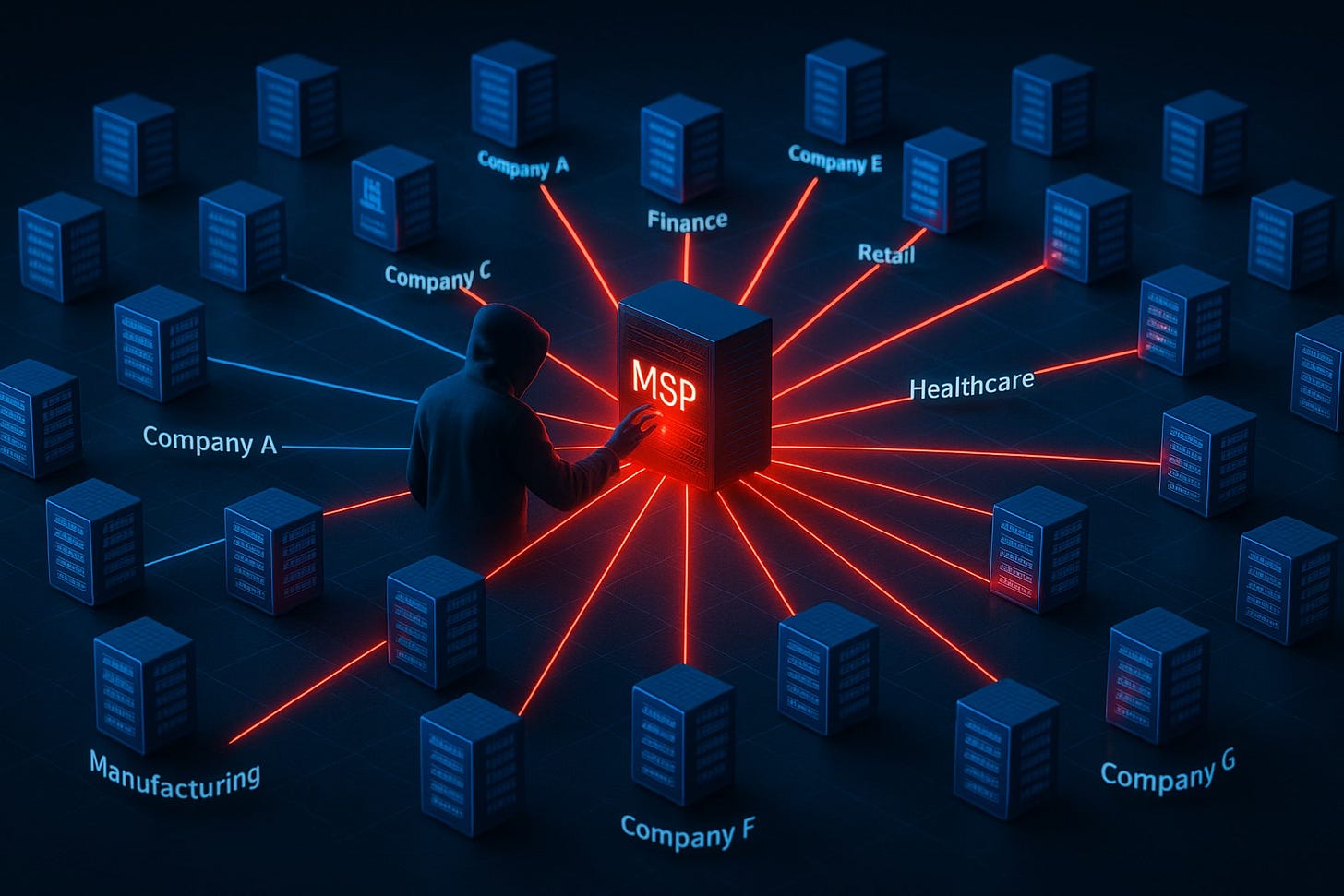
Every month we produce two threat reports for each Critical Infrastructure sector (snapshot and deep dive). A cross-sector analysis of the BRACE platform’s August and September reports revealed the strategic calculus that’s driving current attacker behavior: Why compromise one target when you can compromise their vendor and get fifty?
Supply chain attacks doubled from an average of 13 per month back in April to over 25 in August, with September hitting 31 disclosed incidents in Critical Infrastructure sectors. These aren’t random opportunistic attacks. 63% directly targeted IT, tech, and telecom companies… the vendors with privileged access to everyone else’s networks. [5]
The Strategic Logic Is Brutal
Even before the big news from F5 was released, the Communications Sector had the highest threat rating across all sectors for September at 78.6/100. Compromise one major communications provider and you potentially gain access to thousands of downstream customers and critical data flows. Our reporting documented China’s APT41 and Russia’s APT29 (Cozy Bear) actively targeting MSPs and telecommunications infrastructure specifically to leverage that downstream access. [5]
The pattern repeats with surgical precision across sectors:
SCATTERED SPIDER compromised MSPs with access to multiple banking organizations, then used those credentials to fan out across their client base in what became one of 2024’s most sophisticated financial sector campaigns.
APT29 targeted MSPs servicing defense contractors, leveraging that initial access to reach downstream targets with classified information—exactly the kind of strategic patience you’d expect from Russian intelligence operations.
LAZARUS GROUP went after software and service providers with broad customer bases. In July 2024, they hit WazirX exchange for $234.9 million. Single breach. Multiple potential victims. Maximum return on operational investment. [6]
Healthcare Shows the Same Vulnerability Pattern
Medical billing vendor compromises led to multiple hospital breaches. Attacks on healthcare businesses rose 30% in September while direct provider attacks stayed relatively flat. The hospitals themselves had decent security programs. Their vendors didn’t. But the vendors had legitimate access to patient data—and that’s all that mattered. [7]
The Uncomfortable Truth
Your security posture is determined by your least secure vendor. Every SaaS tool. Every MSP. Every medical billing company. Every payroll processor. Each one represents a potential entry point to your environment—and attackers have figured out this math.
Immediate Actions Required:
If you’re the customer:
Your vendor risk program can’t be an annual questionnaire. You need continuous security requirements in contracts, verified assessments of actual controls (not self-attestation), and liability clauses with teeth.
Implement time-limited credentials for vendor access. Just-in-time provisioning. Session monitoring. Behavioral analytics that flag unusual vendor activity.
Create vendor-specific incident response playbooks. When (not if) a vendor gets compromised, you need a pre-planned response that executes in minutes, not a discovery meeting.
If you’re the vendor:
You’re now a high-value target specifically because of the client access you maintain. Your security must match the sensitivity of data you handle, not your company size.
Threat actors don’t care if you’re a Fortune 500 or a 15-person MSP. They care about the administrative access you have to client systems. That access makes you valuable—and vulnerable.
Implement zero-trust architectures for client connections. Network segmentation. Privileged access management. Multi-factor authentication on everything. You’re defending multiple organizations simultaneously whether you realize it or not.
The Math: One compromised vendor with 50 clients = 50 potential victims. That’s why supply chain attacks became the most efficient vector in the current threat landscape.
The Exploitation Window Collapsed
“Patch within 30 days” is dead. That vulnerability management timeline might as well be measured in geological epochs given current exploitation speeds.
China’s APT40 (Gingham Typhoon) weaponizes vulnerabilities within hours of public disclosure. The BRACE platform’s August-September analysis documented this capability repeatedly. APT40 exploited network appliances and VPN concentrators before organizations finished inventorying affected devices, let alone scheduling maintenance windows.
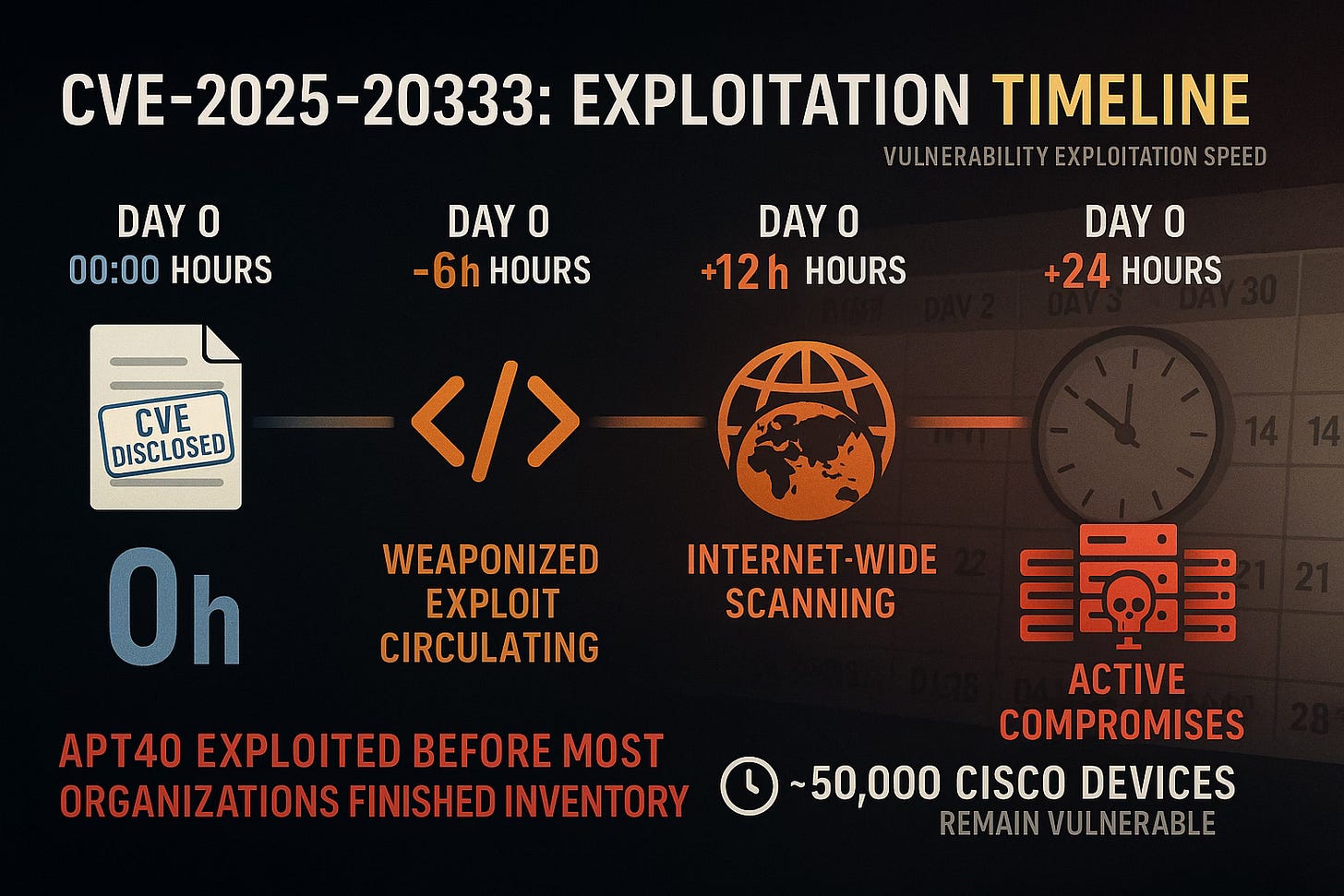
Case Study: CVE-2025-20333
Cisco ASA/FTD firewalls. The vulnerability became a Known Exploited Vulnerability (KEV) with APT40 actively exploiting it in the wild. The timeline tells the story:
Day 0: Public disclosure
Day 0 + 6 hours: Weaponized exploit code circulating
Day 0 + 12 hours: Internet-wide scanning for vulnerable devices
Day 0 + 24 hours: Active compromises documented
All faster than your traditional vulnerability management program can assess risk, let alone deploy patches.
August 2025: Microsoft patched 107 CVEs in one month. Multiple CVSS 9.0+ critical vulnerabilities moved from disclosure to active exploitation in the same week.
Deep Dive: F5 BIG-IP Breach: Practitioner Response Guidance
⚠️ CRITICAL DISCLAIMER: The response actions below are recommended by government agencies and F5. The actions detailed below may impact business operations and system availability. Before implementing any containment, monitoring, or mitigation steps, consult with your cybersecurity vendor, MSP, or internal security team. If you’re uncertain about any procedure, seek expert guidance before execution. Improper implementation could cause service disruptions.
UK NCSC, CISA, and F5 Guidance
Following the F5 breach revealed yesterday, the UK National Cyber Security Centre (NCSC) [UK NCSC Advisory, October 2025], the Cybersecurity and Infrastructure Security Agency (CISA) [CISA Emergency Directive 26-01, October 2025], and F5 itself [F5 Security Advisory, October 2025] issued urgent guidance directing all users of F5 BIG-IP devices to take immediate action to mitigate the risk posed by the theft of source code and vulnerability information by a nation-state threat actor.
CISA Emergency Directive 26-01
For U.S. Federal Civilian Executive Branch (FCEB) agencies, CISA issued Emergency Directive 26-01, with requirements and deadlines that serve as a model for all organizations:
Immediate Actions Required:
Inventory assets: Immediately identify and document all instances of F5 hardware and software, including BIG-IP, BIG-IQ, F5OS, and BIG-IP Next
Harden internet-facing devices: Identify any F5 devices whose management interfaces are exposed to the public internet and remove that access immediately—this is a top priority due to the risk of lateral movement and exfiltration
Patch vulnerable devices: Install the latest vendor updates and security patches released by F5, prioritizing updates for F5OS, BIG-IP TMOS, BIG-IQ, and BNK/CNF by October 22, 2025
Disconnect end-of-life products: Decommission or disconnect any public-facing F5 devices that have reached their end-of-support date
Rotate credentials: Reset all cryptographic keys, certificates, and access credentials, especially for the management plane, to prevent attackers who may have gained access from retaining it
Hunt for threats: Conduct threat hunting and forensic analysis on F5 devices and related systems to detect signs of compromise
Report findings: Federal agencies must submit a report documenting their F5 inventory and remediation actions to CISA
UK NCSC Advisory
The UK National Cyber Security Centre issued guidance identifying when organizations must perform compromise assessment:
F5 BIG-IP devices are internet-facing AND exposed during the threat actor’s access window
Anomalous authentication events detected on F5 systems
Unexplained configuration changes in BIG-IP management interfaces
Unexpected outbound connections from F5 devices
Gaps in logging during critical timeframes
F5 Company Guidance
F5 has provided its own guidance and resources for customers, including security advisories and tools to assist with detection and response:
Install updates immediately: F5’s official blog post and quarterly security notification urge all customers to apply available patches to address the newly disclosed vulnerabilities
Threat hunting guide: F5 has provided a guide for customers to detect indicators of compromise, available through F5 support
Validated containment: F5 worked with independent cybersecurity firms, including CrowdStrike, Mandiant, NCC Group, and IOActive, to contain the breach and review its software supply chain for manipulation. Their investigation confirmed no evidence of malicious modification to the software
Customer communication: F5 is directly contacting a “small percentage of customers” whose configuration or implementation details were exposed during the breach
Extended detection and response (XDR): F5 partnered with CrowdStrike to offer a free EDR subscription to bolster customers’ defenses
What This Means for Organizations
While CISA’s directive is mandatory only for U.S. federal agencies, the requirements are considered best practice for any organization with F5 devices:
Prioritize and expedite patching: Given the nation-state origin of the breach and the theft of source code, attackers likely have a significant advantage in finding new vulnerabilities. Immediate and ongoing patching is non-negotiable.
Address public-facing management interfaces: If any F5 management consoles are accessible from the public internet, they should be taken offline or placed behind a strict firewall immediately.
Assume compromise and hunt for threats: Treat the breach as a credible threat and assume potential compromise. Conduct proactive threat hunting and look for unusual activity on your F5 devices.
Implement additional hardening measures: Beyond patching, follow F5’s hardening guidance, restrict management access to trusted networks, and use the free CrowdStrike EDR offering to enhance your monitoring capabilities.
Questions? Need threat intelligence support?
📞 24/7 Response: (949) 832-6925
📧 Email: contact@intruvent.com
🔐 Platform: BRACE Threat Intelligence | NOVA AI Engine
🌐 Web: www.intruvent.com
The Intruvent Edge provides strategic intelligence from the BRACE threat intelligence platform covering 18 critical infrastructure sectors.
Next Intruvent EDGE Brief: October 30, 2025
Sources & References
¹ Monthly Threat Report: Stay Ahead of Cybersecurity Trends, October 2025
² Techpoint Africa; Paul Hastings LLP; The Bybit Hack: Following North Korea’s Largest Exploit, TRM Blog; The ByBit Heist and the Future of U.S. Crypto Regulation, Center for Strategic and International Studies (CSIS)
³ Cybersecurity Information Sharing Act expires, and other cybersecurity news, World Economic Forum
⁴ Supply Chain Attacks Surge In April–May 2025
⁵ BRACE Threat Intelligence Platform Monthly Threat Reports, August-September 2025, Intruvent Technologies
⁶ 2024 WazirX hack, Wikipedia
⁷ Healthcare ransomware attacks surge 30% in 2025, as cybercriminals shift focus to vendors and service partners, Industrial Cyber
⁸ Marks & Spencer Cyberattack: A Wake-Up Call for Supply Chain Cybersecurity
⁹ CISA Known Exploited Vulnerabilities Catalog, U.S. Cybersecurity and Infrastructure Security Agency
¹⁰ Healthcare Ransomware Attacks Surge 400% - FBI Alert 2025, CyberUpdates365; Federal Bureau of Investigation and U.S. Cybersecurity and Infrastructure Security Agency Joint Advisory
Analysis compiled from BRACE Threat Intelligence Platform sector reports, government advisories, and industry threat intelligence sources. All data current as of October 2025.