Prevent This: The Invisible Worm
When hackers figured out how to hide malware in plain sight, 35,000 developers became Patient Zero for an attack that's spreading through your everyday apps.
What Happened?
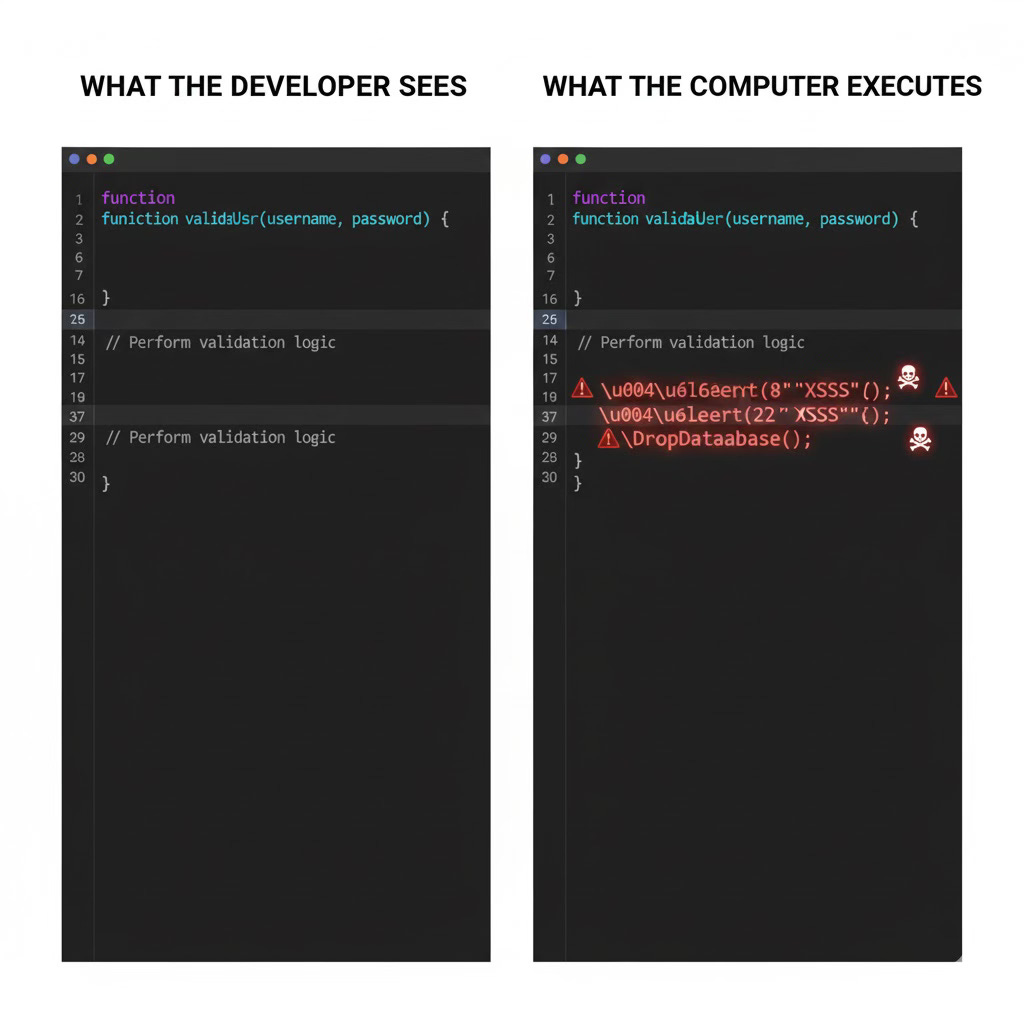
Imagine you’re reading a book, and scattered throughout the pages are invisible sentences written in special ink. You can’t see them. The editor who reviewed the book couldn’t see them. But when you scan the book with your phone’s camera, those hidden sentences tell your phone to send your credit card information to criminals.
That’s essentially what’s happening right now in the world of software development, and it’s called GlassWorm.
On October 17, 2025, security researchers discovered something unprecedented: malware that uses invisible characters to hide itself inside the tools that software developers use every day. Not “hard to see” or “cleverly disguised.” Actually invisible. Like glass, it’s completely transparent. You can stare directly at it and see nothing.
So far, GlassWorm has infected more than 35,800 computers, and as of this writing, it’s still actively spreading. The infected tools automatically update themselves, meaning people are getting hacked without clicking anything, downloading anything, or making any mistakes at all.
Why Should You Care?
Here’s the uncomfortable truth: you might not be a software developer, but everything you use was built by someone who is.
Your banking app? Built by developers. Your smart thermostat? Built by developers. The medical software your doctor uses? Built by developers. Your car’s computer systems? Built by developers.
When a developer’s computer gets infected with malware like GlassWorm, it’s not just their problem. It’s everyone’s problem. Because that developer is now unknowingly building malicious code into the software that millions of people will eventually use.
Think of it like a food supply chain. If bacteria gets into the flour at a factory, it doesn’t just affect the factory workers. That contaminated flour gets baked into bread, shipped to grocery stores, and ends up on dinner tables across the country. By the time people get sick, the contamination has spread to thousands of homes.
Software works the same way. When a developer’s tools get compromised, the malware spreads into every program they touch, which then spreads to everyone who uses those programs. It’s a domino effect that starts with one infected developer and can eventually reach millions of users.
According to cybersecurity experts, these “supply chain attacks” (attacks on the tools and systems used to build other things) are projected to cost businesses worldwide $60 billion in 2025 alone. That’s billion with a B. By 2031, that number is expected to more than double to $138 billion.
And nearly half of all organizations (45%, according to the research firm Gartner) will experience a supply chain attack by the end of this year.
How Did This Actually Work?
Let’s break down what makes GlassWorm so dangerous, using everyday language.
The Invisible Trick
Software developers write code, which is really just instructions that tell computers what to do. They write this code using special programs called “code editors.” Think of them like Microsoft Word, but for writing computer instructions instead of letters.
Normally, when you look at code, you can read it. It might look confusing if you’re not a developer, but you can see the words and symbols on the screen.
GlassWorm uses something called “Unicode variation selectors.” These are special characters that exist in computer language but don’t show up visually. Imagine if your keyboard had invisible keys that didn’t make letters appear when you typed, but the computer still knew you pressed them.
When GlassWorm infects a developer’s tool, it inserts these invisible characters into their code. To the developer looking at their screen, everything appears normal. Just regular code, maybe some blank lines. But when the computer reads that code and runs it, those invisible characters execute malicious commands.
One researcher described it perfectly: “You can stare right at it and see nothing. The developer whose account got compromised probably looked at this file, saw what appeared to be their legitimate code, and had no idea they were about to distribute malware to hundreds of users.”
The Unkillable Network
Most malware operates from a central server. Think of it as a headquarters that sends out commands. If authorities find that server, they can shut it down and stop the attack.
GlassWorm is different. It uses something called “blockchain technology” for its command center. Without getting too technical, blockchain is like a permanent public record that can never be erased or changed once something is written to it. It’s the same technology that cryptocurrencies like Bitcoin use.
The attackers hide their instructions inside blockchain transactions. Since blockchain records can’t be deleted, there’s literally no way to take down GlassWorm’s command center. As one security researcher put it: “You’re playing whack-a-mole with an opponent who has infinite moles.”
And just to be extra safe, GlassWorm has a backup plan: it also hides commands in Google Calendar events. To any security system, it just looks like someone checking their calendar. Who would block that?
The Automatic Spread
Here’s where it gets really scary: GlassWorm is a true “worm” (hence the name).
Traditional malware requires human action to spread. You have to click a bad link, open a suspicious attachment, or download something you shouldn’t. Worms are different. They spread automatically, all by themselves, without any human involvement.
When GlassWorm infects a developer’s computer, it immediately does three things:
First, it steals their passwords and login credentials for systems developers use (things like GitHub, which is basically Google Drive for code).
Second, it uses those stolen credentials to infect other developer tools and projects, automatically, without the attacker doing anything.
Third, it turns the infected computer into part of the attack network, using it to spread to even more computers.
It’s like a zombie infection in a movie: each person who gets infected immediately starts infecting others, creating exponential spread. Each new victim becomes a new carrier.
And remember: most developer tools automatically update themselves. So when an infected update gets published, everyone using that tool gets automatically infected. No warning. No choice. Just silent, automatic infection.
That’s how GlassWorm went from a handful of infected tools on October 17 to over 35,800 infected computers in a matter of days.
The Real-World Impact
Let’s bring this home with a concrete example of what this means in your everyday life.
Remember all those headlines about data breaches over the past few years? “Company X had 50 million customer records stolen.” “App Y leaked user passwords.” Many of those breaches happened because somewhere in the supply chain (in the tools, systems, or code that built that app) something got compromised.
In August 2025, a company called Salesloft had its integration with another company called Drift compromised. Attackers accessed data from over 700 organizations, including access to email systems, cloud storage, and collaboration tools. No one at those 700 companies clicked on anything malicious. They were just using software that had been built with compromised tools.
Or consider what happened earlier this year with Applied Materials, a semiconductor company. One of their suppliers got hit with ransomware, and it disrupted Applied Materials’ entire supply chain, costing them an estimated $250 million in just three months.
These aren’t abstract, theoretical problems. These are real companies, real money, and real consequences that eventually trickle down to you. The person using the banking app, the medical software, or the smart home device.
What Can You Do About It?
I know what you’re thinking: “I’m not a developer. What am I supposed to do about invisible code in tools I don’t even use?”
Fair question. Here’s the honest answer:
For Regular People (Non-Developers):
Understand the risk. The most important thing is awareness. When you hear about a security breach or a company saying they need you to change your password, understand that it might not be because you did anything wrong. It might be because somewhere in their software supply chain, something like GlassWorm got in.
Don’t reuse passwords. If one of your accounts gets compromised through a supply chain attack, attackers will try that username and password combination everywhere. Use unique passwords for every important account (and yes, a password manager is worth it).
Keep software updated. Yes, updates can sometimes bring problems (like GlassWorm), but outdated software with known vulnerabilities is an even bigger risk. It’s like choosing between a new car with occasionally faulty brakes versus an old car with no brakes at all.
Be patient with security measures. When your bank makes you use two-factor authentication or when apps require extra verification steps, those aren’t there to annoy you. They’re there because attacks like GlassWorm are real and dangerous.
Use reputable software. Stick with well-known apps from established companies when possible. While even big companies get hacked, they usually have better security teams and more resources to respond when something goes wrong.
For Companies and Organizations:
Audit your developer tools. If you have a development team, make sure they’re reviewing what extensions, plugins, and tools they’re using. Remove anything that isn’t actively necessary.
Don’t trust automatic updates blindly. Consider disabling auto-updates for developer tools and manually reviewing changes before applying them.
Implement the principle of least privilege. Developers shouldn’t have access to everything in your systems. Only what they actually need to do their jobs.
Have an incident response plan. When (not if) something like GlassWorm hits your supply chain, you need to know exactly what to do: who to call, what to check, how to respond.
Invest in security training. Make sure your team understands supply chain risks. The developer who unknowingly installed GlassWorm probably had no idea they were compromising their entire organization.
The Bottom Line
GlassWorm represents something new and troubling in cybersecurity: attacks that are literally invisible, impossible to take down, and spread automatically through the very tools we use to build the digital world.
The malware itself will eventually be contained, cleaned up, and added to security systems’ detection lists. But the techniques it pioneered (invisible code, unkillable infrastructure, automatic propagation through developer tools) aren’t going away.
We’re seeing a fundamental shift in how attackers think. Instead of going after end users directly, they’re going after the foundation: the tools, systems, and people who build everything else. It’s more efficient, more impactful, and more difficult to defend against.
The developers whose computers got infected probably felt terrible about it. But here’s the thing: they didn’t do anything wrong. They installed a legitimate tool that later got compromised. This could happen to anyone.
That’s the uncomfortable reality of our interconnected digital world. Security is no longer just about protecting yourself from mistakes you might make. It’s about understanding that you’re part of a vast, complex web where someone else’s compromise can become your problem through no fault of your own.
The good news? Awareness is the first step. By understanding these attacks (how they work, why they matter, and what they mean for you), you’re already better prepared than most people.
Stay vigilant. Stay informed. And remember: that app on your phone was built by someone, somewhere, using tools that we all hope stayed secure.
Research Sources: Koi Security, SecurityWeek, BleepingComputer, The Hacker News, Dark Reading
Last Updated: October 27, 2025
Want to dive deeper into cybersecurity threats and what they mean for you? Subscribe to The Intruvent Edge for bi-weekly intelligence that cuts through the noise and gives you actionable insights.