Prevent This: The Hackers Living Inside Your Servers
Chinese government hackers have been hiding inside American organizations for over a year using malware called BRICKSTORM. Last week, CISA, the NSA, and Canada’s cyber team issued a warning.
What Happened?
On December 4, the Cybersecurity and Infrastructure Security Agency (CISA) published a joint threat on a specific nation-state threat. Together with the NSA and Canada’s Cyber Centre, they released an emergency advisory about malware they’ve been tracking through multiple victim organizations. The malware is called BRICKSTORM, and it’s being deployed by Chinese state-sponsored hackers like UNC5221/WARP PANDA, who have one primary goal: get in, stay hidden, and wait.
For those of you who follow me on LinkedIn or Twitter, this will sound familiar. In early September of this year BRACE started lighting up with a massive uptick in attacks by Brickstorm. We moved quickly to publish a threat hunting guide (here) and alerted the community.
What had me concerned in September about this group hasn’t changed in the last weeks: this group is actively burrowing in to the cyber infrastructure of sophisticated US based Tech companies and Law Firms and setting up for the long haul.
CISA is a phenomenal organization and I commend them for publishing their deep dive research on this one. They pulled eight malware samples directly from compromised organizations, including one where they conducted a hands-on incident response engagement. What they found was sobering and confirms our earlier concerns.
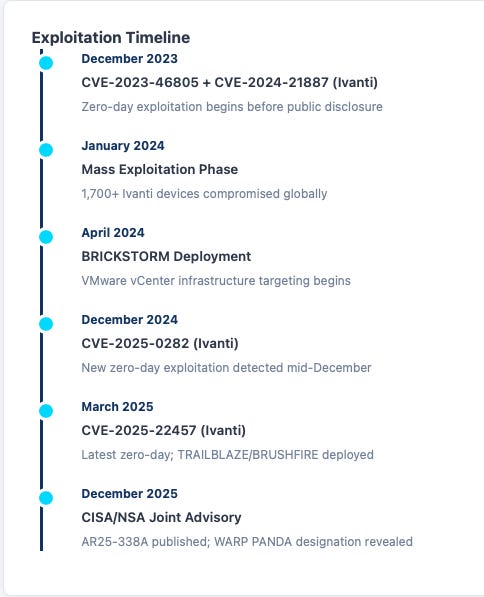
In one confirmed case, attackers gained access to a web server in April 2024. From there, they moved laterally through the network until they reached the organization’s VMware vCenter server, which is essentially the control center for all virtual machines in an environment. They installed BRICKSTORM and maintained access until at least September 2025. That’s seventeen months of undetected presence inside the network.
During that time, the attackers weren’t smashing and grabbing. They were methodical. They accessed domain controllers (where all the access controls are stored). They compromised an Active Directory Federation Services server and exported cryptographic keys (like stealing the master unlock code for an alarm system). They made their own copies of virtual machines to work unfettered and extract credentials. They created hidden rogue VMs that they could power on when needed and shut down afterward to avoid detection.
Why Should You Care?
Here’s what makes BRICKSTORM different from the ransomware attacks you read about every week. Ransomware gangs want money. They break in, encrypt your files, and demand payment. It’s ugly, but it’s transactional.
Nation-state actors like the group behind BRICKSTORM have different objectives. They’re playing a longer game. CISA’s Acting Director Madhu Gottumukkala put it bluntly in the advisory: “These state-sponsored actors are not just infiltrating networks. They are embedding themselves to enable long-term access, disruption, and potential sabotage.”
The word “sabotage” should catch your attention. Here’s the timeline from an upcoming Threat Actor Profile (TAP) on WARP PANDA that will be posted on our threat actors hub later today:
As you can see, that is this Threat Actor “playing the long game.”
If you’ve been following cybersecurity news this year, you’ve heard about Volt Typhoon, another Chinese hacking group that has been pre-positioning itself inside critical infrastructure like power grids, water systems, and telecommunications. The concern isn’t that they’re stealing intellectual property. The concern is that they’re preparing for a potential future conflict by ensuring they can disrupt essential services if tensions escalate.
BRICKSTORM fits the same pattern. The hackers behind it are targeting government agencies, high profile law firms and technology companies. They’re stealing credentials and cryptographic keys. They’re mapping networks and maintaining persistent access. And they’re doing it all while staying invisible.
The technology sector targets include the companies that provide services to everyone. If your law firm uses a cloud provider, if your hospital relies on a managed IT service, if your business depends on any technology vendor, you’re indirectly connected to this threat.
How Did This Actually Work?
BRICKSTORM is what security professionals call a “backdoor.” Think of it like a hidden entrance that attackers install so they can come and go as they please without using the front door.
What makes BRICKSTORM particularly nasty is how hard it is to detect.
Most malware communicates with its controllers using methods that security tools can spot. BRICKSTORM uses something called DNS-over-HTTPS, or DoH (insert Homer Simpson noise here). Normally, when your computer needs to look up a website address, it sends a DNS request that network security tools can monitor. DoH encrypts those requests and sends them through regular HTTPS traffic, the same kind of traffic you generate when visiting any secure website. From a network monitoring perspective, BRICKSTORM’s communications look like someone browsing the web.
Once the attackers establish communication, BRICKSTORM wraps everything in multiple layers of encryption which hides the traffic. Secure web protocol (HTTPS) on the outside, WebSockets underneath, and additional TLS encryption inside that. It’s like a set of nesting dolls, but each layer makes detection harder.
The malware primarily targets VMware vCenter servers. If you’re not familiar with VMware, here’s why this matters: many organizations run their servers as virtual machines. Instead of having one physical server doing one job, they have powerful physical servers running dozens of virtual servers. VMware vCenter is the management console that controls all of it.
Compromising vCenter is like stealing the master key to an entire building. Attackers can see every virtual machine, access their configurations, clone them to extract data, and even create new hidden VMs that don’t show up in normal inventory. That’s exactly what CISA observed in their investigation.
BRICKSTORM also includes a self-healing mechanism. If someone tries to remove it or if the system restarts, the malware checks on itself and reinstalls automatically. The attackers modified system startup files to ensure BRICKSTORM survives reboots. This persistence is one reason the attackers maintained access for seventeen months without being caught.
The Windows variant of the malware extends the threat beyond VMware environments. Now organizations running mixed infrastructure have to worry about BRICKSTORM on both platforms.
What Can You Do About It?
For Everyone
If you work in an organization that uses computers to do business (which is everyone), here are questions you should be asking:
Ask your IT team or managed service provider directly: “Are we protected agains backdoors like BRICKSTORM? What’s our plan for scanning our VMware and Windows environments?”
This isn’t a gotcha question. It’s a reasonable inquiry that any executive, board member, or department head should be making right now. CISA released detection signatures and indicators of compromise specifically so organizations can check whether they’ve been hit.
If you’re on a board of directors: Add this to your next meeting agenda. Ask leadership what the organization’s exposure is to VMware environments and whether the security team has conducted threat hunting for BRICKSTORM indicators.
If you’re a small business owner using a managed IT provider: Send them a quick email. “I saw the CISA warning about BRICKSTORM malware targeting VMware servers. Can you confirm whether this affects our environment and what steps you’re taking to address it?”
Good IT providers will appreciate the question. It shows you’re paying attention, and it gives them an opportunity to demonstrate they’re on top of current threats.
For IT and Security Professionals
Grab our Threat Hunting Guide here.
Here’s your action list:
Scan for BRICKSTORM immediately. The advisory includes YARA and Sigma rules designed to detect the malware. CISA released eight sample analyses, and the detection signatures cover variations in functionality across those samples. Run these against your VMware vCenter servers and Windows environments.
Block unauthorized DNS-over-HTTPS traffic. BRICKSTORM uses legitimate DoH providers like Google (8.8.8.8) and Cloudflare (1.1.1.1) for command and control. Your infrastructure servers should not be making direct DoH connections. If you see HTTPS traffic from vCenter or ESXi hosts to known DoH providers, investigate immediately.
Inventory your network edge devices. The initial access vector in confirmed compromises involved web servers in the DMZ. Know what’s exposed to the internet, and monitor those devices for suspicious activity.
Check your network segmentation. The attackers in CISA’s case study moved from a DMZ web server to an internal vCenter server. If your DMZ can reach internal infrastructure management systems without restriction, you have a problem.
Hunt for credential theft activity. BRICKSTORM operators go after Active Directory. Look for unusual access to domain controllers, ADFS servers, and any system that stores authentication data. Check for unexpected VM cloning operations, especially of domain controllers.
Review VMware account activity. New local accounts on vCenter, permission changes, or SSO modifications could indicate compromise. The attackers need accounts to maintain access, and they’ll create them if they can’t steal existing ones.
Check system initialization files. BRICKSTORM modifies files like /etc/sysconfig/init to survive reboots. Standard memory forensics might miss persistence mechanisms that exist only on disk. Include static file analysis in your hunt.
We’ve published a comprehensive threat hunting guide specifically for BRICKSTORM that walks through ten detection modules covering everything from asset inventory validation to VM cloning detection. You can download it at intruvent.com/brickstorm.
Reporting Requirements
If you find BRICKSTORM or related activity, consider reporting it. This matters. Consult with your legal team and consider contacting your government cyber authority.
For U.S. organizations, contact CISA’s 24/7 Operations Center at contact@cisa.dhs.gov or call 1-844-Say-CISA. When you report, mention that the activity is related to BRICKSTORM so they can route you to the right team.
For Canadian organizations, email the Cyber Centre at contact@cyber.gc.ca.
CISA specifically requests that organizations submit malware samples through their Malware Analysis Submission Form. The more samples they collect, the better they can track the evolution of this threat and provide updated detection guidance.
The Bottom Line
BRICKSTORM represents a category of threat that doesn’t grab headlines the way ransomware does. There’s no dramatic ransom demand, no website defacement, no immediate chaos. Instead, there are patient attackers sitting inside networks for months or years, collecting credentials, mapping infrastructure, and positioning themselves for future operations.
The joint advisory from CISA, NSA, and Canada’s Cyber Centre is a clear signal that this threat has reached a level where public warning is necessary. They analyzed samples from multiple victim organizations. They conducted incident response at a compromised site. They found attackers who had maintained access for over a year.
If your organization runs VMware infrastructure or Windows servers, assume you could be a target. Run the detection signatures. Block unauthorized DoH traffic. Hunt for the indicators of compromise. And if you find something, report it.
The attackers behind BRICKSTORM are playing a long game. The only way to counter that is to find them before they’re ready to act. We are always here to help. Ping me on substack or reach out at contact@intruvent.com. Happy Hunting!
For the complete threat hunting guide with detection queries, YARA rules, and step-by-step hunt modules, visit our page here.
Research Sources: CISA/NSA/Cyber Centre Joint Malware Analysis Report AR25-338A (December 4, 2025), CISA Alert on PRC State-Sponsored BRICKSTORM Activity, Google Mandiant Threat Intelligence, CrowdStrike Warp Panda Analysis
Last Updated: December 9, 2025