Intruvet EDGE / The WSUS Vulnerability Being Actively Exploited
Zombie servers rise from their graves to cause havoc across the world.
When Your Update System Becomes the Attack Vector: The Critical WSUS Exploit Unfolding
Executive Summary
On Tuesday we had ghost code. Today we are going to talk about zombie servers and how they are rising from their graves to affect corporate networks across the globe. HAPPY HALLOWEEN!
Windows Server Update Services (WSUS) was killer technology when it launched in 2005 in a pre-cloud world. A stalwart of the security infrastructure, these servers would receive patches from the Microsoft mothership and then send them out to the other computers in the environment.
Since 2010, though, the writing has been on the wall. Microsoft stopped developing WSUS and added no real new features since then. In the summer of 2024 Microsoft announced listed WSUS status as “features removed or no longer developed starting with Windows Server 2025.” Then in the fall of 2024, Microsoft officially announced WSUS as being depreciated (outdated software that is no longer supported).
So most of the world moved on to newer and better technologies. But many organizations forgot about these former key servers and left them connected to the Internet in some dusty part of the organization. Now, thanks to a critical vulnerability, they have become an open doorway to attackers.
What Happened?
A critical remote code execution vulnerability, CVE-2025-59287, in Windows Server Update Services (WSUS) has been actively exploited since October 23, 2025. With a CVSS score of 9.8, this flaw is particularly dangerous because of WSUS’s strategic position inside corporate environments. By compromising a single WSUS server, attackers can hijack the entire patch distribution system for a company and push malware disguised as legitimate updates to every endpoint in an organization. The very mechanism organizations use for protection becomes the weapon against them.
The Vulnerability Landscape
Transparency Note: Microsoft is a sponsor of Intruvent Technologies. This analysis is based on independent security research, vendor advisories, and threat intelligence from multiple sources across the cybersecurity community. Our coverage aims to provide objective, actionable intelligence regardless of vendor relationships.
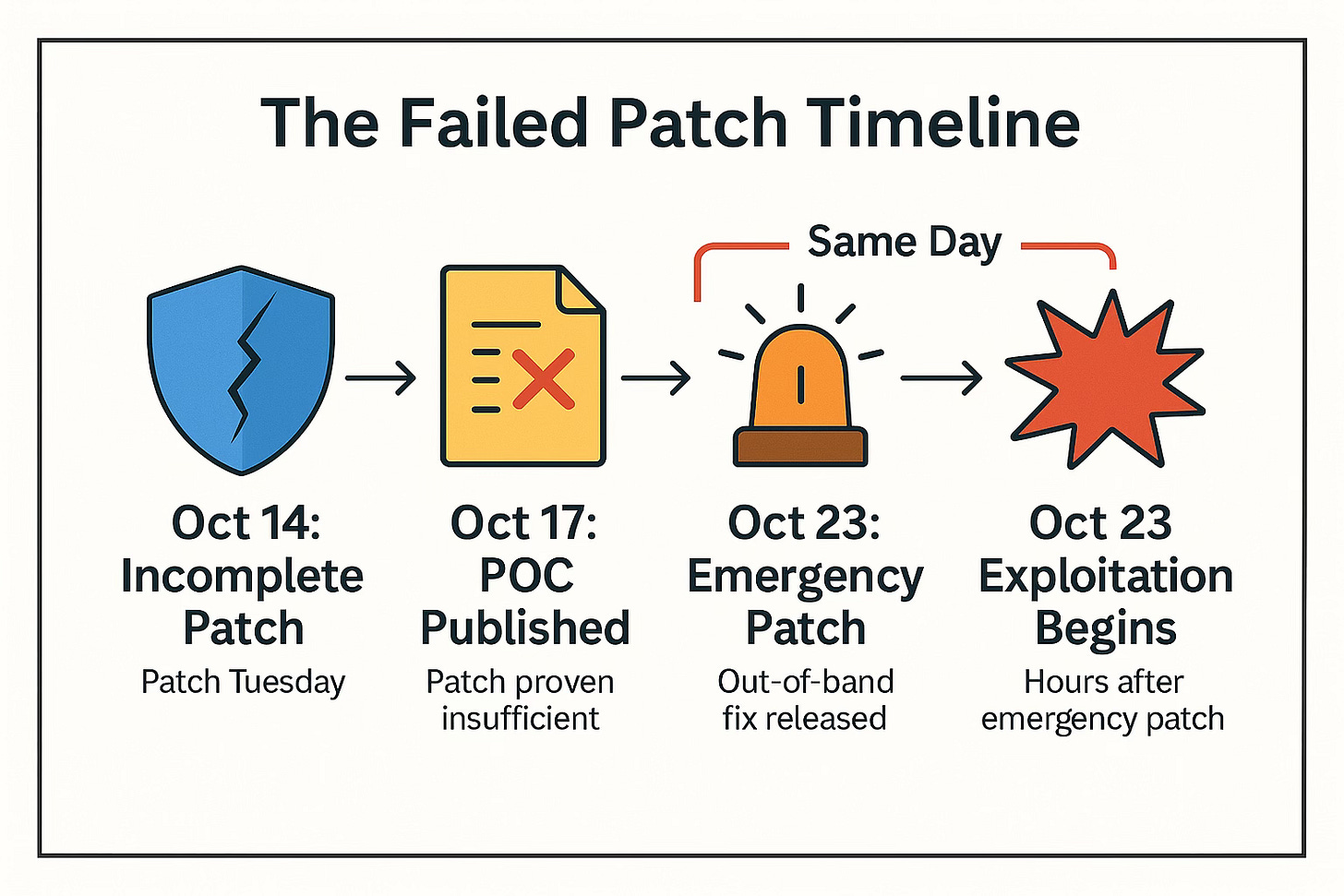
Microsoft initially addressed CVE-2025-59287 during October Patch Tuesday on October 14, 2025, but the fix proved incomplete. An emergency out-of-band security update followed on October 23. Within hours, active exploitation began, prompting CISA (the Cybersecurity and Infrastructure Security Agency) to add the vulnerability to its Known Exploited Vulnerabilities catalog and instructing all US federal agencies to patch by a November 14 deadline.
Hours after the emergency patch was released, Google’s Threat Intelligence Group identified a new threat actor, UNC6512 actively exploiting the flaw across multiple organizations. The weaponization timeline from proof-of-concept publication to active exploitation took mere days.
Understanding the Technical Attack Surface
CVE-2025-59287 is an unsafe deserialization vulnerability. Deserialization converts code or data into a usable format, and becomes dangerous when the process doesn’t verify what’s in the data. Think of it like accepting and opening a package without checking who sent it.
Microsoft’s own security documentation warns that BinaryFormatter.Deserialize, the legacy .NET mechanism at this vulnerability’s core, “is never safe when used with untrusted input” and “can’t be made secure”. Microsoft has warned developers away from BinaryFormatter for years, yet critical infrastructure still relies on it.
The vulnerability allows remote, unauthenticated attackers to send specially crafted requests that execute malicious code with SYSTEM-level privileges. No user interaction required. No authentication needed.
Exploitation in the Wild
The solid folks over at Huntress as well as the Google team mentioned above, observed threat actors beginning exploitation on October 23, 2025, hours after teh emergency patch was released. These attackers are targeting publicly exposed WSUS instances on ports 8530 and 8531. Attacks spawned Command Prompt and PowerShell via WSUS binaries, with Base64-encoded payloads that enumerated servers for sensitive information and exfiltrated results to remote webhooks.
Remember those anonymous packages that we talked about earlier? This would be like opening a big box that arrived at your house and having three burglars jumping out and robbing you.
Eye Security detected sophisticated attacks using ysoserial.net gadget chains with embedded PE (Portable Executable) files—capabilities “beyond that of a script kiddie,” suggesting state-sponsored actors or advanced ransomware gangs.
Trend Micro’s telemetry shows approximately 100,000 exploitation attempts in seven days, with nearly 500,000 internet-facing servers potentially vulnerable. Palo Alto Networks identified approximately 5,500 WSUS instances exposed globally. So this is a big problem…
Underground Intelligence Note: Intruvent’s monitoring indicates proof-of-concept exploit code surfaced on underground forums shortly after Microsoft’s initial patching guidance on October 15. Security researchers report ransomware groups like LockBit 3.0 referenced the POC in their leak sites. While we cannot independently verify the full extent of underground activity, the rapid weaponization timeline and attack sophistication suggest organized criminal interest from the beginning of this attack cycle.
Microsoft’s Response and the Patch Trust Problem
The vulnerability affects Windows Server 2012 through 2025 with WSUS Server Role enabled. Microsoft’s out-of-band (subsequent) update is cumulative and requires system rebooting.
Dustin Childs from Trend Micro’s Zero Day Initiative notes that incomplete patches increase risk by signaling false security. Organizations applying the initial October Patch Tuesday update may have believed they were protected when they weren’t.
Tactical Defensive Measures: What You Need To Do Now
Immediate Actions (Next 24-48 Hours):
Identify Your Exposure
Identify all servers with WSUS Server Role enabled and ports 8530/8531 accessible
Use network scanning to discover any WSUS instances, including forgotten servers in branch offices or test environments
Check for publicly exposed instances immediately
Apply Emergency Patch
Install the out-of-band update KB5070883 for all supported Windows Server versions and reboot systems
Prioritize internet-facing instances, then work inward
Document patch status across your server inventory
Implement Temporary Workarounds (If Patching Delayed)
Disable WSUS Server Role temporarily, or block inbound traffic to ports 8530 and 8531 on host firewalls
Understand this prevents update distribution until patches are applied
Don’t undo workarounds until after patching is complete
Short-Term Hardening (Next 1-2 Weeks):
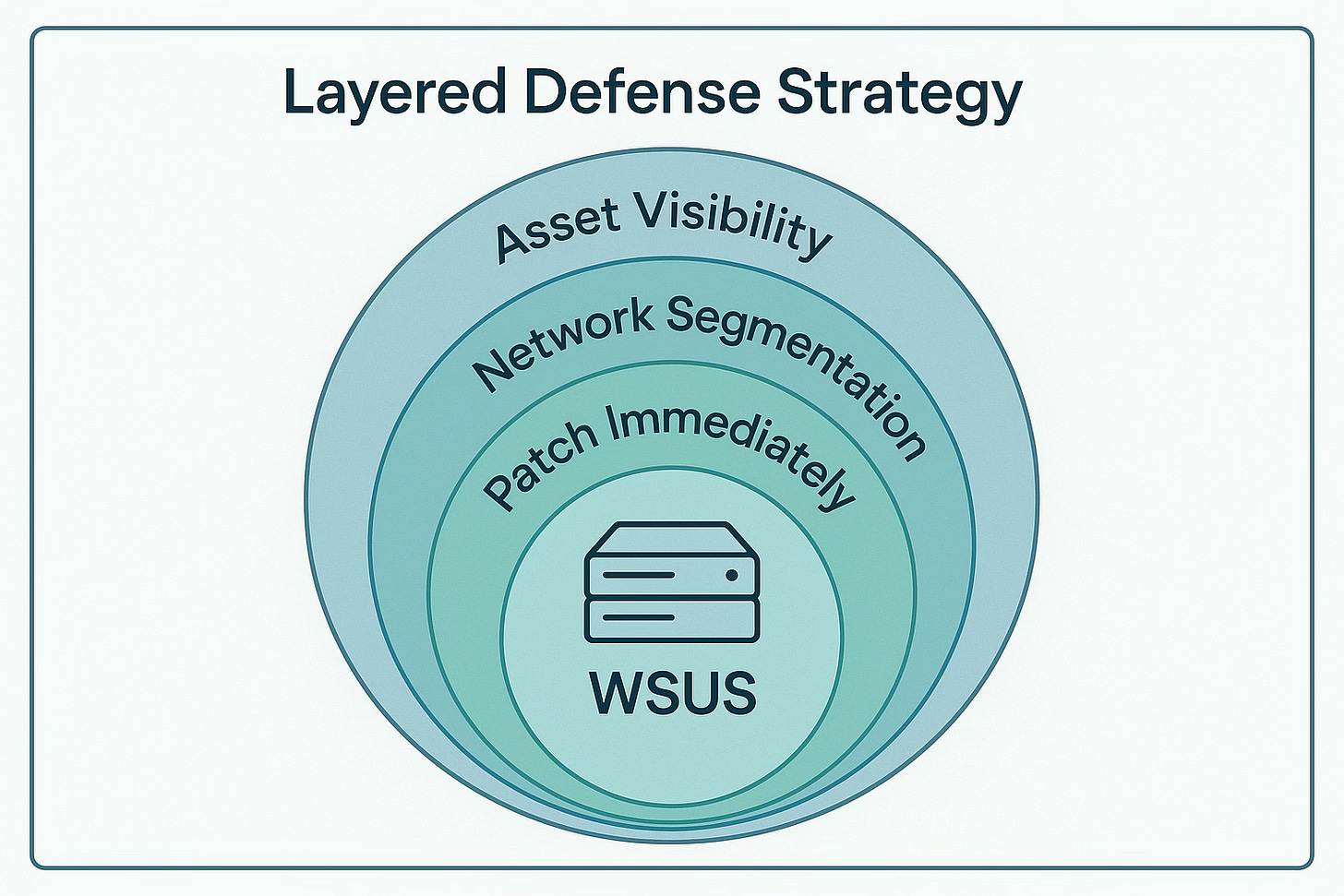
Network Segmentation Review
Ensure WSUS servers are operated behind firewalls and never exposed to the internet
Implement strict access controls limiting WSUS management to trusted admin networks only
Review and eliminate any internet-accessible paths to WSUS infrastructure
Threat Hunting and Detection
Search for suspicious cmd.exe and powershell.exe spawned via grandparent processes w3wp.exe and wsusservice.exe
Check WSUS log files at %ProgramFiles%\Update Services\LogFiles\SoftwareDistribution.log for deserialization errors or suspicious stack traces
Look for unauthorized connections to WSUS web services
Monitor for data exfiltration to unusual webhook or external sites
Forensic Investigation (If Compromise Suspected)
Assume compromise if WSUS was internet-accessible and unpatched during the exploitation window
Investigate whether malicious updates were distributed to endpoints
Check for lateral movement or persistence mechanisms
Consider engaging incident response capabilities
Long-Term Security Posture (Next 30-90 Days):
Infrastructure Modernization Assessment
Evaluate migration away from deprecated WSUS to modern update management solutions, as Microsoft isn’t adding new features and organizations often adopt a “set it and forget it” posture
Consider Windows Update for Business, Microsoft Endpoint Manager, or other modern alternatives
Document technical debt and create remediation roadmaps
Asset Management Overhaul
Implement continuous asset discovery and inventory
Develop processes ensuring all internet-facing services are known, authorized, and monitored
Create regular reviews of external attack surface
Least Privilege and Segmentation
Ensure WSUS servers operate with minimal privileges necessary
Enforce network segmentation with zero-trust principles
Implement micro-segmentation where feasible for critical infrastructure
Enhanced Monitoring
Deploy EDR (Endpoint Detection and Response, advanced security software that monitors and responds to threats) solutions across all servers
Use endpoint detection tools to detect deserialization-based attacks
Establish baselines for normal WSUS behavior and alert on deviations
Integrate WSUS server logs into SIEM (Security Information and Event Management, centralized security monitoring) platforms
Strategic Takeaways
Don’t Let Your Infrastructure Become a Zombie
Remember our WSUS server from the comic? That progression from champion to threat isn’t just creative storytelling - it’s playing out in networks right now.
Here’s what I’ve learned responding to hundreds of similar incidents:
Trusted systems are high-value targets. The same trust that makes these systems powerful makes them dangerous when compromised. If you trust it, so do your users…and that’s exactly what attackers exploit.
Perfect patches can’t save bad architecture. I’ve seen breaches where every system was “fully patched” but basic misconfigurations left critical infrastructure exposed. Configuration management isn’t sexy, but it’s essential.
Technical debt comes due with interest. Microsoft has been telling us to move away from WSUS for years. Every quarter you delay migration is another quarter attackers have to develop techniques against deprecated technology.
Your patching pipeline needs protection too. When the system responsible for security becomes the vulnerability, single-layer defenses fail. Defense-in-depth isn’t paranoia…it’s survival.
The Bottom Line
CVE-2025-59287 represents more than another critical vulnerability. It’s a case study in how attackers exploit technical flaws, configuration mistakes, and trust in infrastructure systems. The vulnerability affects the very mechanism designed to keep systems secure.
Organizations with WSUS infrastructure should patch immediately, harden ruthlessly, and begin planning migration away from deprecated technologies. The next CVE-2025-59287 will arrive. The question is whether you’ll be ready.
The difference between a protected network and a breached one comes down to which systems you stopped paying attention to.
Stay vigilant out there.
Research Sources:
Bitdefender Technical Advisory
Google Threat Intelligence Group (GTIG)
CISA Known Exploited Vulnerabilities Catalog
Palo Alto Networks Unit 42
Huntress Threat Research
Eye Security Research
Microsoft Security Response Center
Dutch National Cyber Security Centre (NCSC-NL)
Trend Micro Zero Day Initiative
Microsoft .NET Security Documentation
Last Updated: October 29, 2025





Great info! Love the spooky twist. Very well explained! Excellent remediation strategy. Thank you for sharing