Intruvent EDGE: Security Infrastructure Under Siege
Nation-State Actors Exploit the Devices Meant to Protect Everything Else
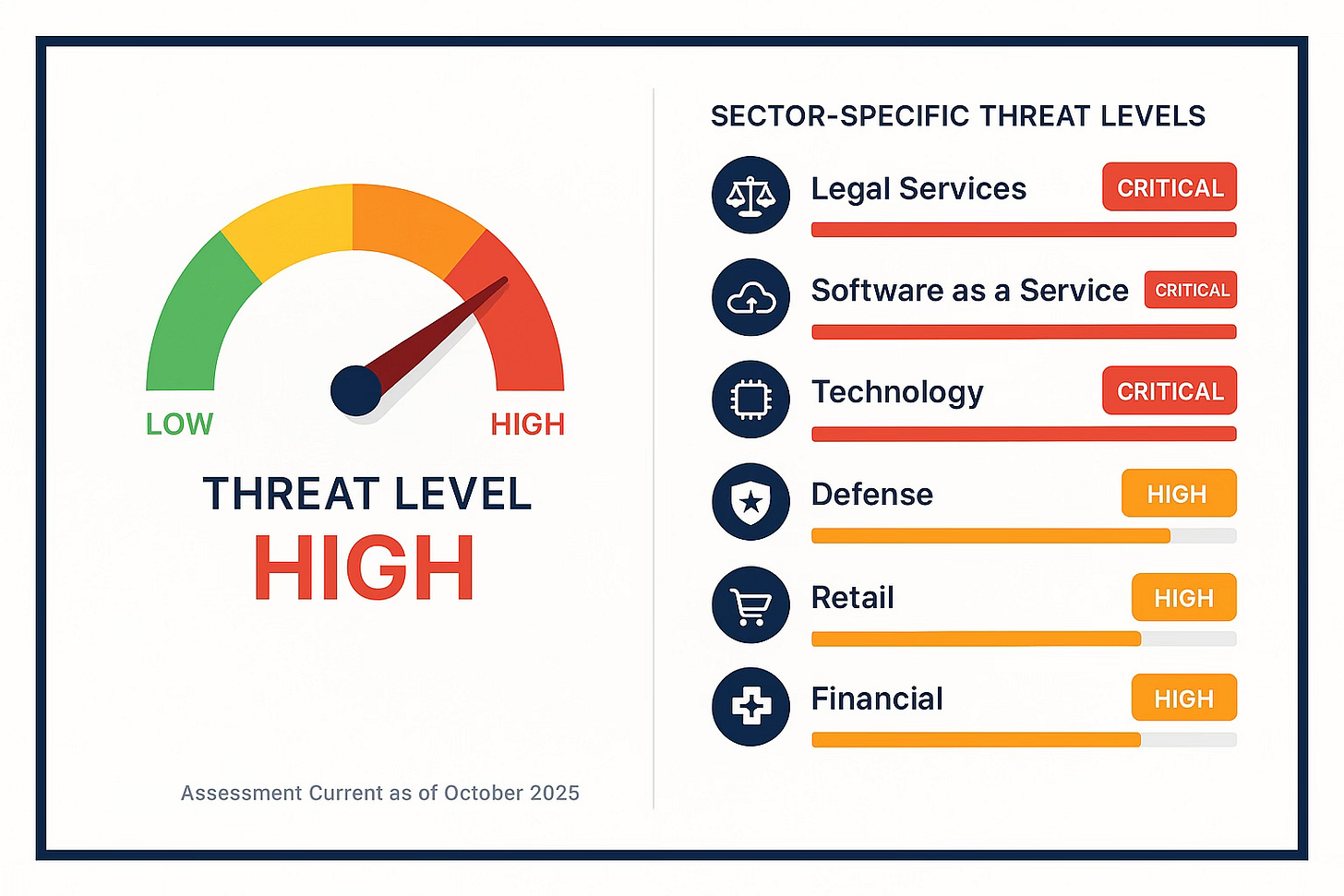
THREAT METER: HIGH
WHAT YOU NEED TO KNOW
Three state-sponsored groups from China are establishing long-term presence on edge and security devices. They are specifically targeting legal and technology companies in the US.
In the last 24 hours, attacks targeting U.S. government and defense firms have skyrocketed. This is likely a planned response to the government shutdown.
Early warning signals show that FIN7 is gearing up to target U.S.-based retail companies.
North Korean fake IT workers have expanded into Europe and the Gulf states. Geographic assumptions about targeting no longer apply
IMMEDIATE ACTION
Hunt in VMware vCenter NOW: If you’re in legal/Technology/SaaS, threat actors have been inside similar environments for over a year. Don’t wait for alerts. We have a free BRICKSTORM Threat Hunting checklist on the website here
EXECUTIVE SNAPSHOT
(table showing active APT threat actors and their targets)
ANALYST NOTES
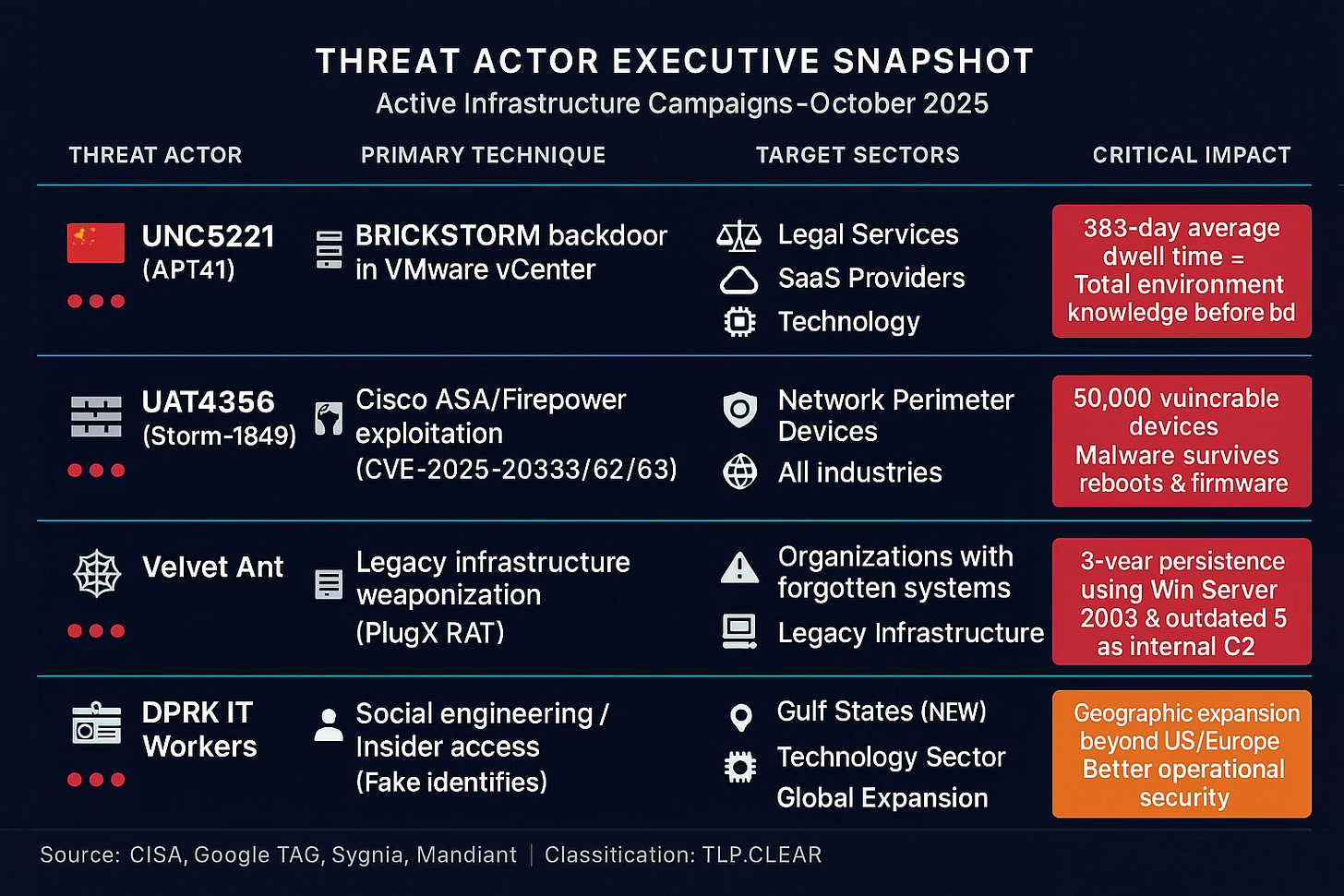
UNC5221 (APT41 | China): Harvesting Strategic Intelligence
What They’re Doing: Living inside VMware vCenter servers using BRICKSTORM backdoor, masquerading as legitimate web server processes. They’re not attacking your endpoints… they’re compromising the platform that manages ALL your virtual machines.
Why It Works: vCenter doesn’t support EDR agents, and its web traffic is expected to be heavy. By the time you discover them, your initial breach logs have aged out (their avg. dwell time of 393 days > 90-day retention).
Who Should Act: Legal firms handling trade negotiations, SaaS providers, and technology companies. They’re targeting strategic intelligence and supply chain opportunities.
Take Action: Download our complete BRICKSTORM Threat Hunting Guide with step-by-step detection procedures, QuickStart guide (30-60 minutes), and 24/7 incident response contacts.
UAT4356 (Storm-1849 | China): Firewall Takeover
What They’re Doing: Chaining CVE-2025-20333 + CVE-2025-20362 to achieve unauthenticated remote code execution on Cisco ASA and Firepower devices. They’re turning your firewalls into attack platforms.
Why It Works: The malware (RayInitiator bootkit) manipulates read-only memory, surviving reboots and firmware upgrades. Your primary security control is now their persistence mechanism.
Attack Surface: ~50,000 devices remain vulnerable. These aren’t workstations you can patch overnight. They’re critical infrastructure requiring change windows.
Dark Web Intelligence: Non-nation-state actors are now actively discussing these vulnerabilities in underground forums, preparing to exploit the same attack chains.
Velvet Ant (China): The Legacy System Hunter
What They’re Doing: Weaponizing forgotten infrastructure (Windows Server 2003, outdated F5 BIG-IP) to establish internal C2 that works even when external communications are blocked.
Why It Works: These systems aren’t in your CMDB, don’t have EDR, and nobody remembers they exist. When defenders thought they’d eradicated the threat, it resurfaced within days from redundant footholds.
Timeline of Persistence:
Year 1: Initial compromise of legacy F5/Windows Server 2003
Year 2: Lateral movement to modern infrastructure, EDR disabled
Year 3: Internal C2 via file servers — survives external blocking
↓
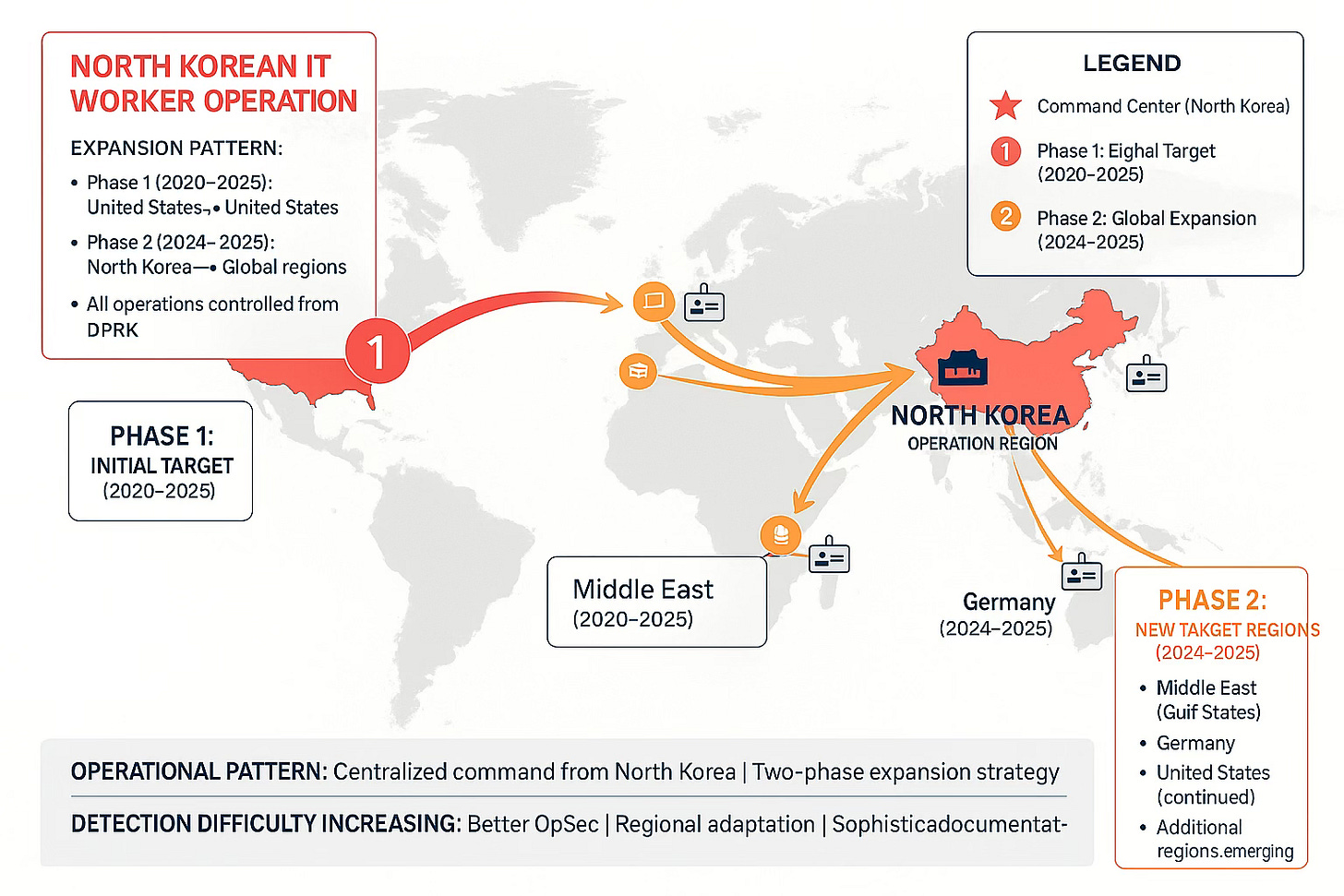
Result: Multiple eradication attempts failed due to backup footholdsDPRK IT Workers (North Korea): Geographic Expansion
What’s Changed: Fake IT worker operations have expanded beyond US/UK into Europe and the Gulf states. We have direct intelligence from two Gulf organizations with suspected infiltrations.
Why It Matters: Geographic assumptions about DPRK targeting no longer apply. Regions that saw minimal North Korean activity are now discovering these operations.
New TTPs: More sophisticated identity documentation, location metadata matching claimed regions, communication patterns adapted to regional norms.
Geographic Expansion:
FIN7 (Carbanak | Russia): Infrastructure Financing Surge
What We’re Seeing: Financial transactions observed on dark web marketplaces show FIN7 establishing new infrastructure through Post Ltd (Russia) and SmartApe (Estonia), with communications across multiple Stark Industries-assigned hosts. The funding patterns indicate preparation for a major campaign launch, likely targeting financial and retail sectors based on historical preferences.
Why This Matters: The group has built over 4,000 hosts employing various exploits, from typosquatting and booby-trapped ads to malicious browser extensions and spearphishing domains, with new domains surfacing as recently as April 2025. The financial activity we’re tracking suggests they’re scaling operations beyond their current capacity.
Technical Evolution: FIN7 has enhanced operations with new EDR bypasses, automated SQL injection attacks, and their AvNeutralizer tool that’s being marketed in criminal underground markets. They’ve introduced custom loaders including PowerNet (decompresses NetSupport RAT) and MaskBat (obfuscated FakeBat variant).
Who Should Be Concerned: Given the infrastructure investment we’re tracking, expect expanded targeting across multiple verticals, starting with Retail. FIN7 recently targeted automotive, transportation, insurance, and defense sectors in addition to their traditional retail, restaurant, and hospitality focus.
STRATEGIC DEFENSE FRAMEWORK
WEEK 1: STOP THE BLEEDING
Critical Security Patches (Require Maintenance Windows)
CISCO ASA/FIREWALL - CRITICAL (⚠️ Maintenance window required)
Patch CVE-2025-20333, CVE-2025-20362, CVE-2025-20363
Impact: HIGH - Network security interruption
VMWARE VCENTER - CRITICAL (⚠️ Maintenance window required)
Apply all security updates
Impact: MEDIUM - VM management disruption
F5 BIG-IP - HIGH (⚠️ Maintenance window required)
Audit/update outdated firmware
Impact: MEDIUM - Traffic redirection needed
Hunt for Active Compromises (Start Immediately - No Downtime)
vCenter Servers: Look for workers.dev connections
Network Appliances: Search for WRITE_LOG variables
Forgotten Systems: Find Windows Server 2003, old F5 devices
MONTHS 1-3: BUILD PROPER DETECTION
Traditional EDR doesn’t work on network gear
Infrastructure Monitoring
HIGH PRIORITY: Network-based detection for infrastructure
Disruption: MEDIUM - Network config changes required
MITRE Defense: D3-CSAA
HIGH PRIORITY: Log aggregation for non-forwarding devices
Disruption: LOW-MEDIUM - Brief service interruption
MITRE Defense: D3-CSAA
MEDIUM PRIORITY: File integrity monitoring on appliances
Disruption: MEDIUM - Performance impact possible
MITRE Defense: D3-CSAA
Persistence Detection
These attacks survive reboots and firmware updates
Bootkit Detection: Requires planned reboots to test
SSH Backdoor Monitoring: No downtime required
Memory Analysis: May impact device performance
MONTHS 3-12: ARCHITECTURAL CHANGES
Zero Trust for Infrastructure
HIGH IMPACT: Network Microsegmentation
Business Impact: HIGH - Multiple maintenance windows
Planning Required: EXTENSIVE - Architecture redesign
Benefit: Contain infrastructure compromises
MEDIUM IMPACT: Certificate-Based Authentication
Business Impact: MEDIUM - Device reboots needed
Planning Required: MODERATE - Certificate lifecycle management
Benefit: Eliminate credential-based attacks
MEDIUM IMPACT: Privileged Access Management
Business Impact: MEDIUM - Temporary access restrictions
Planning Required: MODERATE - User training required
Benefit: Controlled infrastructure access
⚠️ CHANGE MANAGEMENT CHEAT SHEET
COORDINATE THESE CHANGES (High Business Impact)
Cisco firewall patching - Network security downtime
VMware vCenter updates - All VMs affected
Network microsegmentation - Fundamental architecture change
SCHEDULE DURING OFF-HOURS (Medium Impact)
F5 load balancer updates
Network monitoring configuration changes
Certificate deployment
IMPLEMENT GRADUALLY (Low Impact)
Identity verification processes
Threat intelligence integration
Documentation and playbook updates
THE BOTTOM LINE
The Problem: Advanced attackers understand your security architecture. They design their attacks to last years. They’re living in the systems you trust to protect everything else.
The Solution: Start treating security infrastructure as attack targets, not just protective controls.
The Priority: Week 1 actions prevent active exploitation. Everything else builds long-term resilience.
The Reality: Three Chinese groups, expanding North Korean operations, and resurgent Russian cybercriminals all prove the same point: traditional security boundaries can be compromised.
Time to adapt your defenses accordingly.
INTELLIGENCE SOURCES
CISA Emergency Directives
Google Threat Intelligence Group
Sygnia Threat Research
Mandiant UNC5221 Analysis
Intruvent Intelligence Collection
Questions? Need help threat hunting?
24/7 Incident Response: (949) 832-6925
BRICKSTORM Hunting Resources: https://www.intruvent.com/brickstorm
Platform: BRACE Threat Intelligence
Next Intruvent EDGE Brief: October 16, 2025
Intruvent Edge Newsletter — Strategic cyber threat intelligence for security leaders