Intruvent EDGE: November Threats by the Numbers (and Beyond)
A ransomware cartel is formed. Akira has a banner month. And credentials are the skeleton key for all Critical Infrastructure sectors
November 2025: Cyber Threat Roundup
Every month, customers of our BRACE platform get sector-specific reports delivered direct to their inbox. The reports include a detailed analysis of the threat actors that are actively targeting their sector, how to defend against those threat actors, and how to hunt for their presence in the customer’s environment.
Multiple clients asked if they could get a cross-sector threat report which would look at broader trends targeting the Critical Infrastructure sectors. What a great idea! So we added that this month. You can see the report here. The results were striking…
We’ll get into that in a minute. Before we do, I have an ask for you all. If you know anyone in a cybersecurity role in a critical infrastructure org, please send them our Volt Typhoon Threat Hunting guide (here). I don’t care about the “credit” or generating sales for this one. We’ve been tracking this threat group, and they are quickly expanding across multiple additional sectors. See “The Quiet War: China’s Infrastructure Pre-Positioning Continues” below. We need to get the word out!
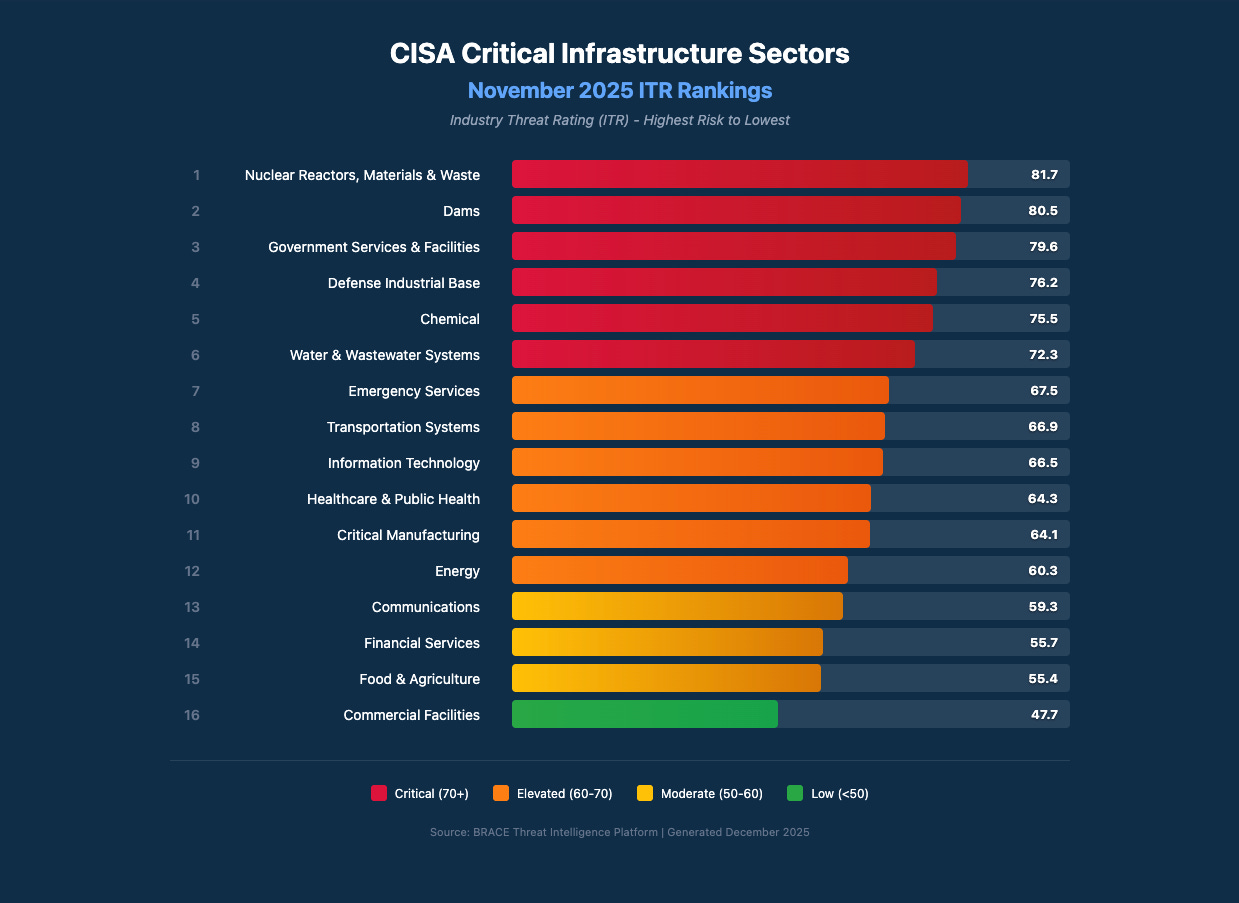
OK, on to the monthly roundup! Below is a graph showing the Intruvent Threat Rating (ITR) for each critical infrastructure sector. The ITR is calculated across 4 dimensions: Threat Actor Pressure, Vulnerability Exposure, Attack Success Rate and Attack Sophistication.
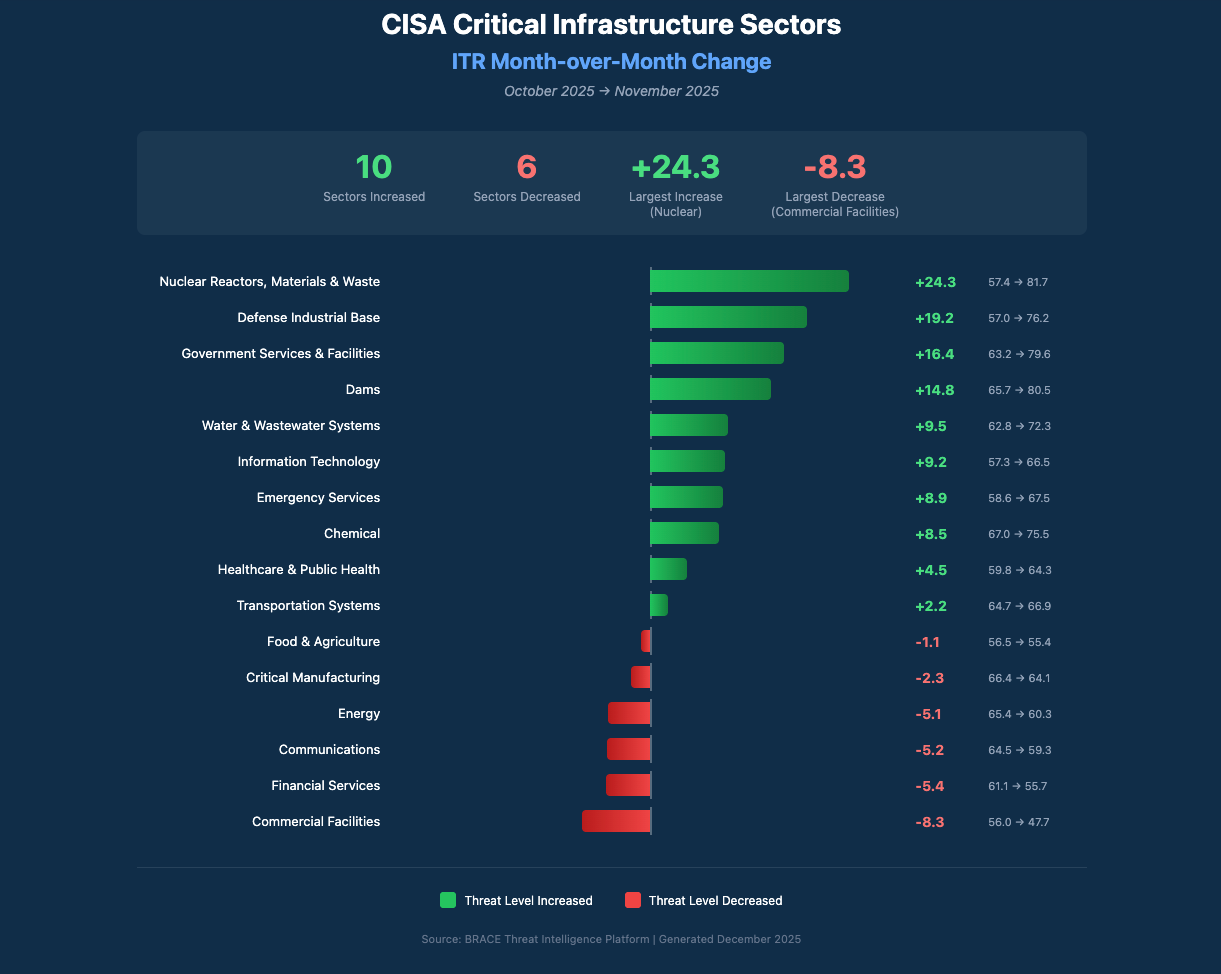
Here is the monthly change for each sector:
Many of the sectors show large increases due to new threat actors targeting the sector and increased successful attacks.
Beyond the numbers, as we started to explore the data across sectors certain notable stories came into focus. In the pages below, we will cover some of these stories.
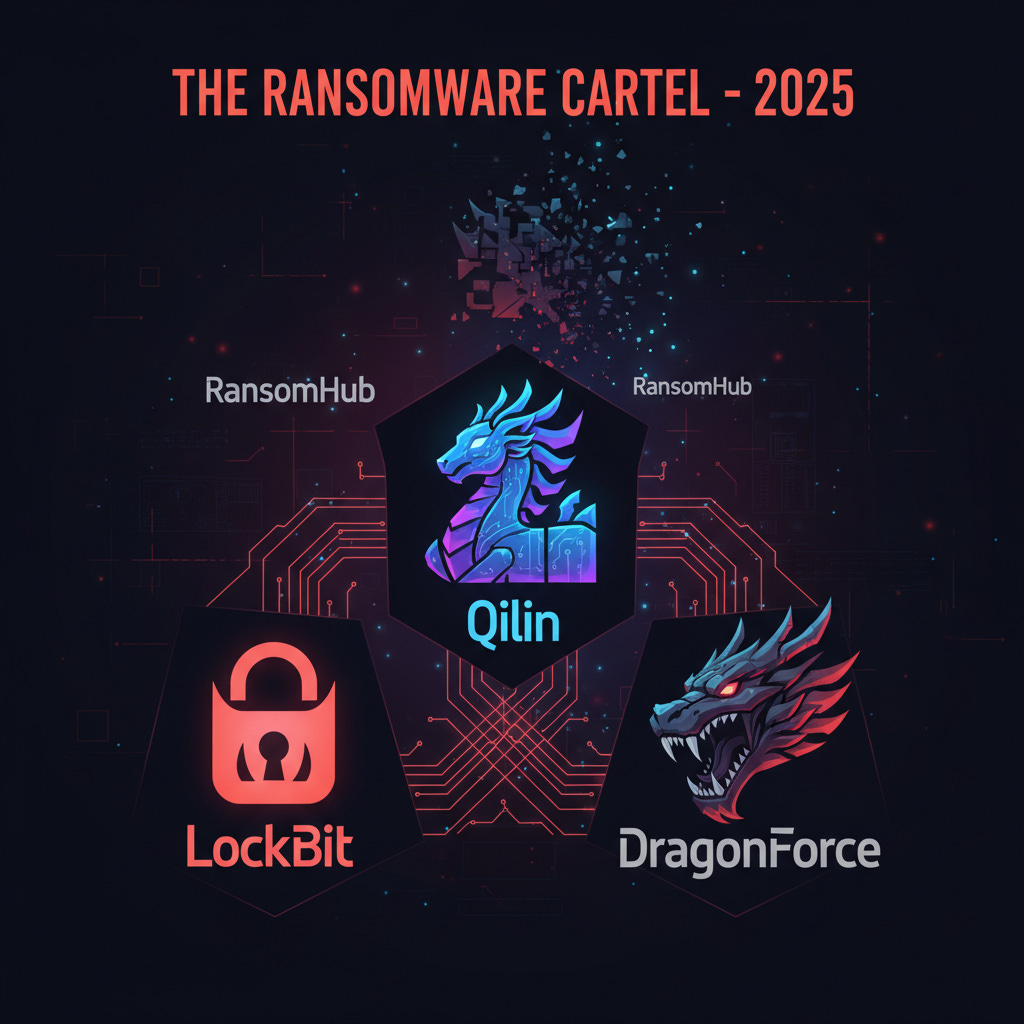
The New Order: Ransomware’s Cartel Era Begins
For years, the ransomware ecosystem operated like competing franchises. Rival groups fought for affiliates, undercut each other on ransom splits, and occasionally sniped victims from one another. That model appears to be over.
Following RansomHub’s collapse in April 2025, three of the most capable ransomware operations have done something we haven’t seen at this scale: they’ve formed a coordinated cartel. LockBit 3.0, Qilin, and DragonForce are now sharing infrastructure, affiliates, and strategic targeting priorities. Security researchers at ReliaQuest have traced shared infrastructure, tools, and data-leak resources linking all three groups.
The timing tells the story. LockBit spent 2024 recovering from Operation Cronos, the multinational law enforcement action that seized their infrastructure and exposed their internal communications. By September 2025, they launched LockBit 5.0 on the RAMP darknet forum, timed to their affiliate program’s sixth anniversary. The new version targets Windows, Linux, and ESXi systems, includes anti-analysis features to block investigators, and uses randomized 16-character file extensions to evade detection.
DragonForce, meanwhile, claimed to have taken over RansomHub’s data leak site in April 2025. What began as a hacktivist collective has evolved into a commercially-motivated extortion operation. Their malware has been reused by other cybercriminals, including Scattered Spider.
Qilin rounded out the alliance after claiming more than 200 victims in Q3 2025 alone. Their operations have a corporate polish: standardized negotiation processes, consistent branding, and a “Call Lawyer” feature designed to increase pressure on victims.
Why this matters for defenders: Cartels mean efficiency. Instead of three separate groups independently developing capabilities, you now have pooled resources. Affiliate networks that previously served one group can rotate between operations. A victim who refuses to pay LockBit might find Qilin knocking next, with full knowledge of the failed negotiation.
Q3 2025 saw over 1,400 ransomware and digital extortion incidents globally. The days of ransomware groups as chaotic independent operators are giving way to something more organized.
Akira: How One Group Conquered 81% of Critical Infrastructure
Akira ransomware didn’t just have a good November. They achieved something approaching market dominance, successfully targeting 13 of 16 critical infrastructure sectors and collecting an estimated $244 million in ransom payments.
The question security teams should be asking goes beyond “how do we defend against Akira.” The real question is how one group achieved this kind of reach.
The affiliate model on steroids: Akira’s success comes from operational scale more than technical sophistication. Their affiliate program has attracted experienced operators, many of whom migrated from disrupted groups like BlackCat/ALPHV. These aren’t newcomers learning the trade. They’re professionals who brought established access and proven playbooks.
The VPN vulnerability pipeline: Akira’s primary initial access vector remains VPN appliance exploitation, specifically SonicWall, Ivanti, and Fortinet devices. The November data shows this approach is systematic, not opportunistic. Akira affiliates appear to be running continuous scanning operations against internet-facing VPN infrastructure, weaponizing new CVEs within days of disclosure.
Double-extortion refinement: Akira has refined the pressure campaign. Their leak site operates on predictable schedules, their negotiators follow scripts optimized through hundreds of engagements, and their data exfiltration happens before encryption. Organizations with solid backups still face the publication threat.
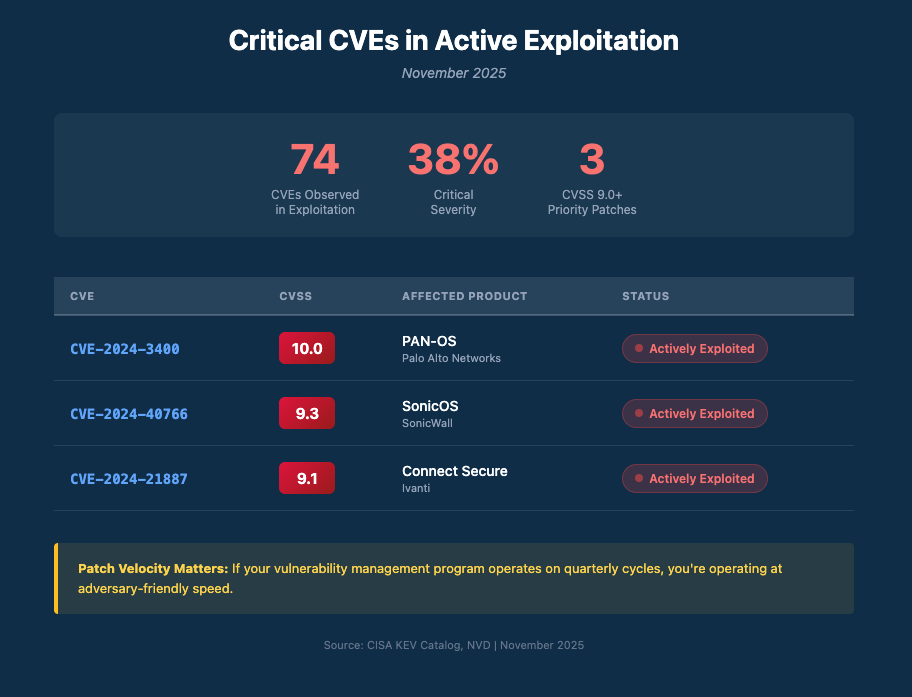
Defensive priorities: The report identifies CVE-2024-40766 (SonicWall, 9.3 severity), CVE-2024-3400 (Palo Alto, 10.0), and CVE-2024-21887 (Ivanti, 9.1) as the most exploited vulnerabilities. If your organization runs any of these appliances, patch status should be verified this week. MFA on VPN access is the difference between being a target and being a victim.
November by the Numbers: Five Trends Demanding Attention
The cross-sector data from November reveals patterns that extend beyond any single threat actor. These are ecosystem-level shifts that security leaders need to understand.
OT/ICS Targeting: +45% Month-over-Month
Attacks against operational technology environments increased 45% compared to October 2025. [Editor’s note: October 2025 set the previous record… So we are starting from an already bad spot.] November saw 13 distinct OT/ICS-focused threat signals identified across critical infrastructure sectors. This acceleration reflects adversary interest in systems that control physical processes in energy, water, manufacturing, and transportation.
The convergence of IT and OT networks, accelerated by remote monitoring requirements, has created attack surfaces that many organizations haven’t fully mapped. Adversaries are doing that mapping for them.
AI-Enabled Attacks: +120% Year-over-Year
Detected instances of AI-assisted attack components more than doubled compared to the same period in 2024. This statistic requires context. We’re seeing AI-generated phishing content that defeats traditional detection, automated reconnaissance that operates at machine speed, and polymorphic malware that rewrites itself to evade signatures.
The defensive implications are significant. Security tools trained on historical attack patterns are increasingly encountering content that doesn’t match those patterns. Organizations relying solely on signature-based detection are falling behind.
Third-Party Breaches: +100% Year-over-Year
Supply chain compromise doubled compared to 2024. Threat actors have learned that compromising one managed service provider yields access to dozens or hundreds of downstream victims. The economics are simply too attractive.
The uncomfortable reality: your security posture is only as strong as your least-secure vendor with privileged access to your environment.
Government Ransom Demands: +85% Year-over-Year
Ransom demands targeting government entities increased 85% compared to 2024. Ransomware groups are increasingly willing to target government organizations despite the heightened law enforcement attention this brings. The calculation appears to be that government victims, particularly local and state agencies, often lack mature security programs while controlling systems that deliver essential services. The pressure to pay is enormous when constituents can’t access services.
Healthcare Ransom Demands: -91% Year-over-Year
This is the outlier that demands explanation. Average ransom demands against healthcare organizations dropped from $4 million in 2024 to $343,000 in 2025, according to the Sophos State of Ransomware in Healthcare report. Actual payments fell from $1.47 million to $150,000, the lowest across all sectors surveyed.
Several factors are driving this shift. Attackers are moving toward extortion-without-encryption tactics, which tripled to 12% of attacks from 4% in 2022/2023. Meanwhile, successful encryption events dropped to 34% from 74% the previous year as defensive measures improved. Nearly 60% of healthcare providers now recover within one week, up from just 21% last year.
The cautious interpretation: adversaries are adapting tactics, not retreating. Healthcare remains a high-value target. The 88 distinct threat groups that Sophos X-Ops observed targeting healthcare in the past year confirms this sector isn’t getting a reprieve.
The Quiet War: China’s Infrastructure Pre-Positioning Continues
Volt Typhoon’s presence in 8 critical infrastructure sectors isn’t news to readers of this newsletter. What’s notable in November’s data is the continued expansion despite significant public exposure.
The sectors where Volt Typhoon maintains presence tell the story: Chemical. Dams. Communications. Water and Wastewater. Government Services. Food and Agriculture. Energy. Emergency Services. Defense Industrial Base.
Most threat actors, when their operations are detailed in government advisories and security vendor reports, adapt by changing infrastructure, retiring compromised tooling, or shifting focus. Volt Typhoon has done none of these things. The living-off-the-land techniques that make them difficult to detect continue unchanged. The sector targeting, focused on systems that would matter in a geopolitical crisis, remains consistent.
The strategic read: This activity doesn’t fit traditional espionage patterns. The intelligence value of pre-positioning in water treatment facilities or dam control systems is minimal. What these positions provide is capability: the ability to disrupt physical infrastructure if strategic circumstances require it.
For security teams, the challenge is detection. Volt Typhoon doesn’t bring custom malware that triggers alerts. They use valid credentials, native system tools, and legitimate remote access pathways. Detecting them requires behavioral analysis and anomaly detection that many organizations haven’t implemented. [Editor’s note: We need to act on this! Grab our threat hunting guide here. Send it to your colleagues, email it to your friends. Let’s get the word out!]
The November data shows Nuclear Reactors (81.7 ITR), Dams (80.5, +15% month-over-month), and Government Services (79.6, +16% month-over-month) at the highest threat ratings. These aren’t random targets. They’re the systems that matter most if competition becomes conflict.
The Universal Vulnerability: Why Credentials Are the Skeleton Key
One finding from November deserves its own callout: MITRE ATT&CK technique T1078 (Valid Accounts) appeared in all 16 monitored sectors, used by 32 distinct threat actors.
Every sector. Nearly every major threat actor. One technique.
This isn’t a vulnerability you can patch. Organizations have built environments that trust authenticated users, and adversaries have gotten exceptionally good at obtaining legitimate credentials through phishing, infostealers, access brokers, and breach data reuse.
The attack chain data makes this concrete. The most common sequence observed:
Valid Accounts → Exploit Public-Facing Application → Remote Services → Data Encryption → Exfiltration
The attack starts with credentials. Everything else follows.
Immediate actions: MFA everywhere, but especially on VPNs and remote access. Privileged access management that limits what credentials can do even if compromised. Credential monitoring services to detect exposure in breach datasets. Session monitoring for anomalous authentication patterns.
This is the defensive investment with the highest cross-sector return.
Quick Reference: November’s Critical CVEs
74 CVEs were observed in exploitation across November’s incidents. 38% were critical severity. If your vulnerability management program operates on quarterly cycles, you’re operating at adversary-friendly speed.
Sources
BRACE Threat Intelligence Platform — Sector research, ITR scores, incident correlation
CybelAngel — LockBit, Qilin, and DragonForce alliance analysis (November 2025)
Sophos — State of Ransomware in Healthcare 2025
CrowdStrike — Global Threat Report 2025
Trellix — OT Threat Report (November 2025)
BlueVoyant — Supply Chain Defense Report (November 2025)
Gartner — GenAI Blind Spots Report (November 2025)
Hornetsecurity — Cybersecurity Report 2026
The Intruvent Edge is published bi-weekly by Intruvent Technologies. For questions about specific threats or to discuss how these trends apply to your sector, contact us at intruvent.com.