Intruvent EDGE: From Espionage to Sabotage: Critical Infrastructure's Threat Evolution
471 Reports, 167 Threat Groups, One Alarming Pattern: Attackers are "pre positioning" themselves in our Critical Infrastructure networks. What do they want and what can we do to find them?
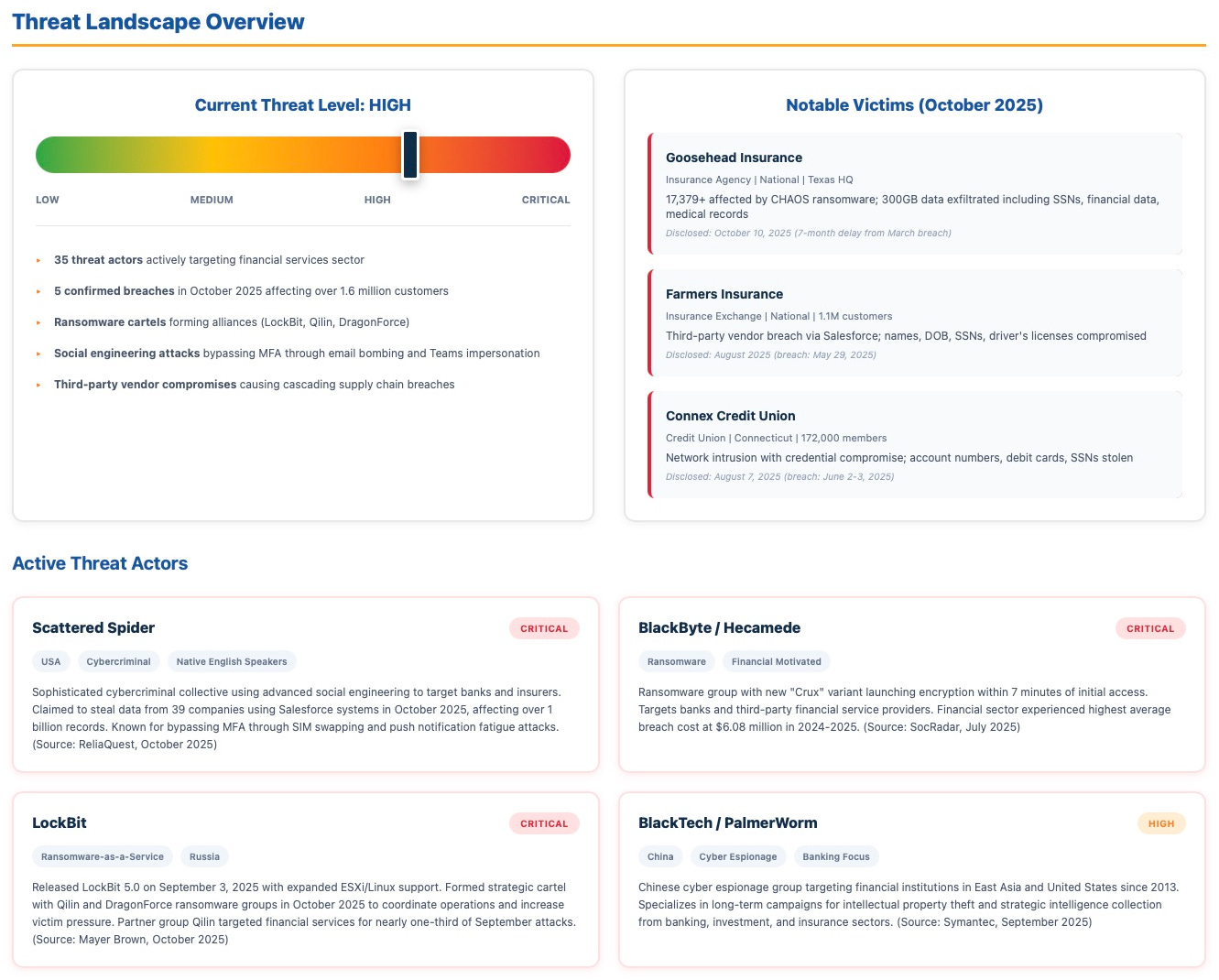
Analysis Period: October 1-31, 2025 | 471 Threat Reports | 167 Threat Groups Tracked
Come Fly With Us: Join the BRACE Pilot Program
Each month Intruvent releases our sector specific BRACE Cyber Threat Intelligence (CTI) detailing threats facing the critical infrastructure sectors. We release two reports for each sector:
Snapshot Report: 2-3 page summary of the threats in the sector
Deep-Dive Report: 15-25 page report covering the threat actors targeting the sector, how they are attacking, how to defend against them, how to detect them, and how to threat hunt for them in your environment.
If you’d be interested in participating in the last two months of our free pilot program, let me know by pinging me here on SubStack or emailing at pilot@intruvent.com. Here’s a quick snippet of the upcoming Financial snapshot covering October:
Executive Summary
BRACE is designed to have a designated “human in the middle” of the process and I happen to be that designated human. Our platform gathers intelligence from all over the Internet and Dark Web, harvests it for metadata and then uploads it into the BRACE platform for review. Then all that glorious intelligence sits there and waits for me to determine if it is going to be published to our database or be cast off into the Island of Misfit Toys.
BRACE handed me 471 threat intelligence reports in October. As I went through them, I noticed an alarming trend: adversaries targeting critical infrastructure are ramping up their operations, and they are moving beyond data theft. Many attack groups are pre-positioning for future attacks…. And some are preparing to test or execute attacks that could have physical disruption capabilities.
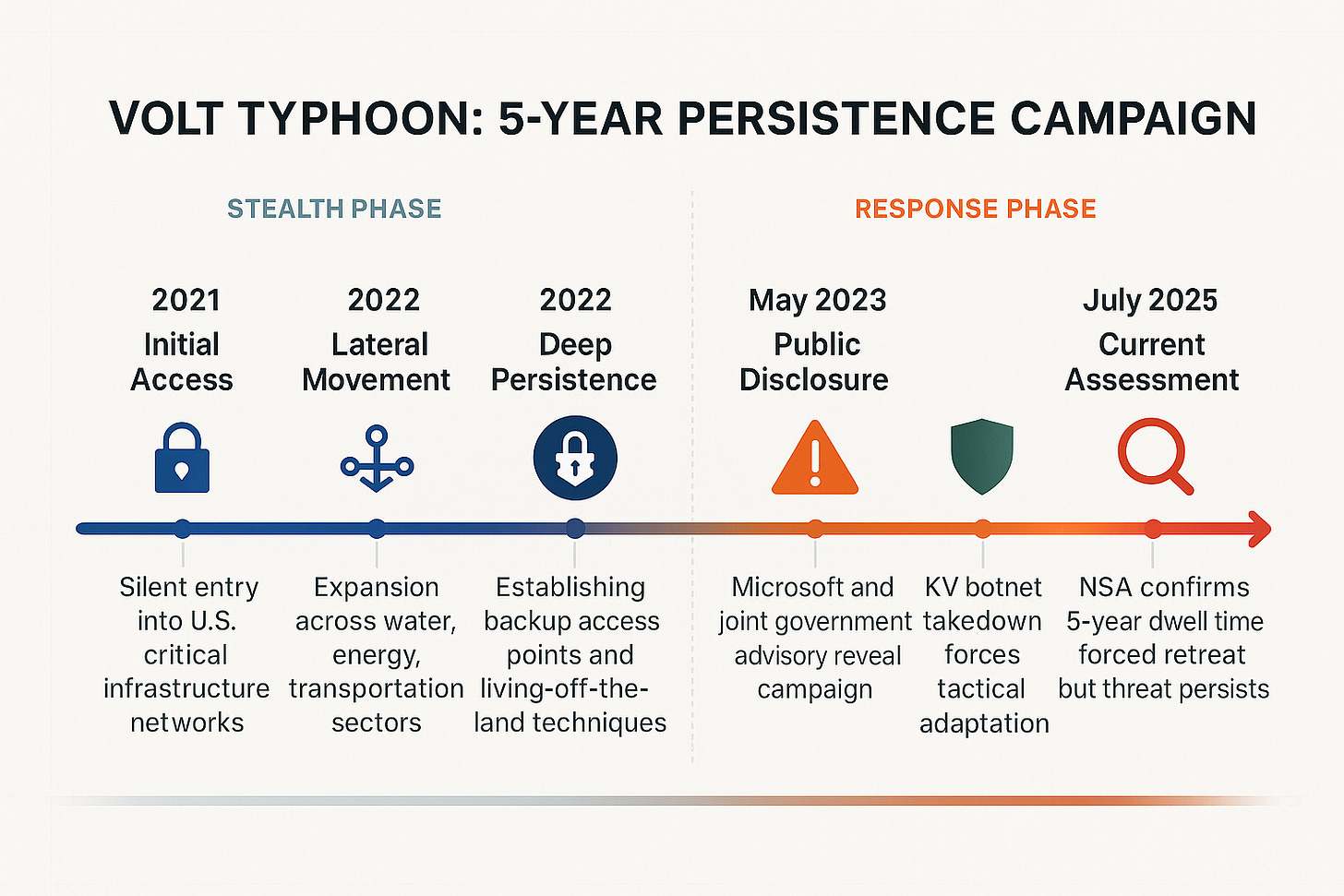
According to joint advisories from CISA [Cybersecurity and Infrastructure Security Agency], NSA, and FBI, Chinese state-sponsored actors including Volt Typhoon have maintained access within some victim IT environments for at least five years. They’re positioning themselves for disruptive or destructive cyberattacks against U.S. critical infrastructure in the event of a major crisis or conflict with the United States. The implications extend beyond cybersecurity. This represents capability staging for geopolitical contingencies.
Key Findings:
230 of 471 threat reports (49%) indicated that attackers were targeting ICS (Industrial Control Systems) and SCADA (Supervisory Control and Data Acquisition) systems. These are the systems that have the ability to cause real-world physical effects
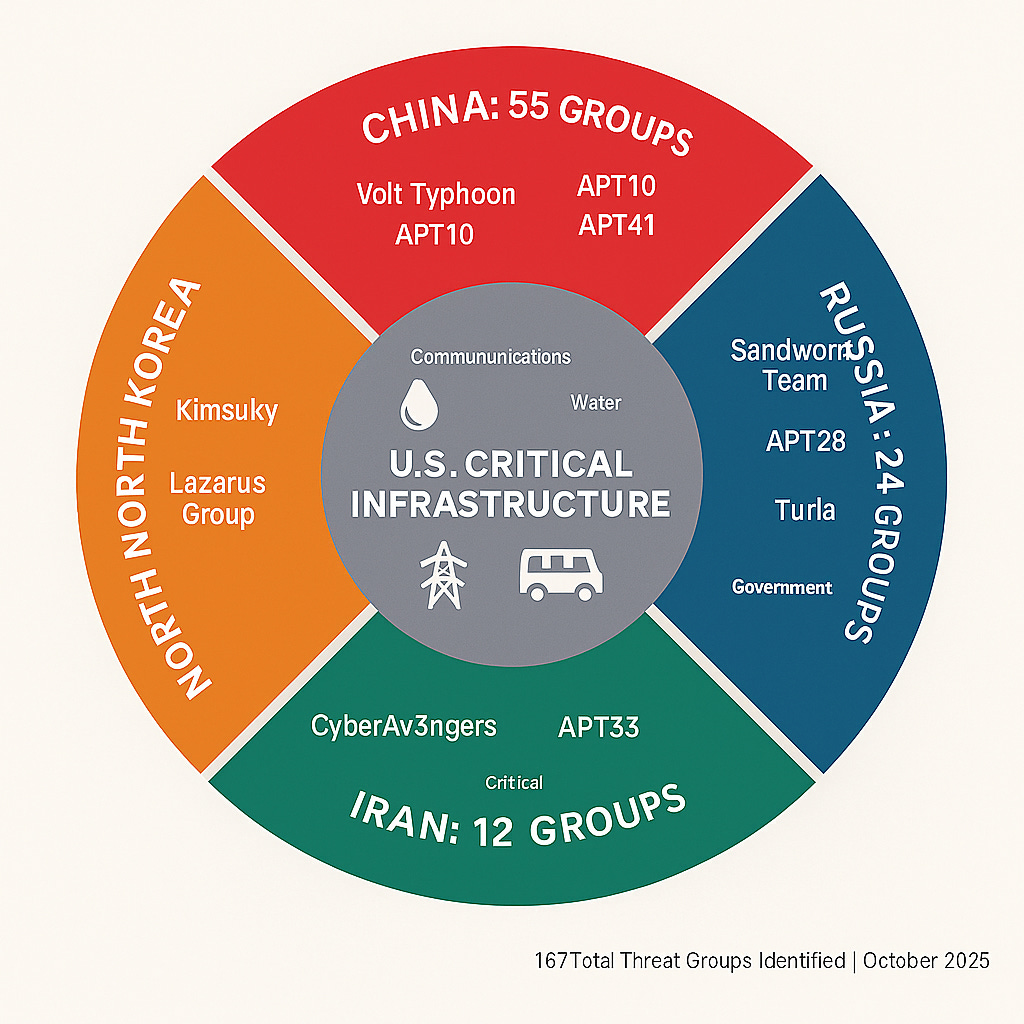
167 distinct active threat groups were reported, with Chinese nation-state actors showing the highest activity at 55 groups
Supply chain attacks demonstrate cascading failure potential across interconnected infrastructure
Multiple attack groups are trying to manipulate cyber targets to have real-world effects
From Digital Theft to Physical Manipulation
The 230 reports focused on industrial control systems represent a fundamental threat evolution. Attackers are no longer just stealing data. They’re manipulating systems that control physical processes: water treatment chemical dosing, power grid voltage regulation, transportation cargo management, and manufacturing production parameters.
ICS refers to the hardware and software that monitors and controls industrial equipment. SCADA systems are a type of ICS that collects data from sensors and instrumentation across large physical infrastructures like power grids, water treatment plants, and pipelines. When adversaries compromise these systems, they gain the ability to manipulate physical processes, not just access digital information.
The Volt Typhoon Blueprint
Volt Typhoon is a Chinese state-sponsored threat actor that’s been active since mid-2021 [Microsoft Security Blog]. The group focuses on achieving unauthorized access through what the security community calls “living off the land” techniques. Instead of deploying custom malware that security tools might detect, they use legitimate system administration tools already present in the target environment: PowerShell, Remote Desktop, Mimikatz, and PsExec.
Think of it this way: a burglar who uses tools from your own garage draws less suspicion than one carrying a bag of lockpicks. Security systems designed to detect “foreign objects” miss threats that use the home’s own tools.
In July 2025, NSA officials confirmed that while Volt Typhoon actors wanted to persist quietly in domestic networks for extended periods, defensive efforts including public advisories forced Chinese actors to pull back and adapt their tactics [The Record]. The publicity “burned” previously effective methods. However, Air Force cyber leadership continues to warn that these threats could enable China to wage destructive cyberattacks against critical infrastructure should regional conflict occur over Taiwan [DefenseScoop].
Volt Typhoon Tactics Summary:
Initial Access: Exploitation of public-facing applications, particularly unpatched VPN appliances from vendors like Fortinet and Citrix
Persistence: Using valid accounts and creating scheduled tasks to maintain access
Credential Access: Dumping operating system credentials and extracting the NTDS.dit file (Active Directory’s main database containing password hashes)
Lateral Movement: Moving between systems using remote services and Pass-the-Hash techniques
Collection: Staging data for exfiltration
Detection Opportunities:
Look for:
Off-hours access to SCADA/ICS networks from IT systems
Engineering workstations communicating with unusual cloud infrastructure
Parameter changes to industrial processes outside normal maintenance windows
Lateral movement between segmented IT/OT (Operational Technology) networks
Water Infrastructure: The Accessible Target
Between November 2023 and January 2024, Iranian IRGC (Islamic Revolutionary Guard Corps) affiliated actors known as CyberAv3ngers targeted U.S.-based Unitronics PLC (Programmable Logic Controller) devices [CISA Advisory AA23-335A]. PLCs are specialized industrial computers that control machinery and processes in manufacturing plants, water treatment facilities, and other critical infrastructure. They compromised at least 75 devices including at least 34 in the water and wastewater sector. The method? Authenticating to internet-connected devices using default passwords or no passwords at all.
The Aliquippa, Pennsylvania incident exemplifies the vulnerability. Hackers accessed the Municipal Water Authority’s pressure regulation system, forcing a switch to manual operations [The Record]. Officials confirmed no risk to the actual water supply, but the incident demonstrated how easily attackers could access critical systems. The attackers left defacement messages reading “You have been hacked, down with Israel. Every equipment ‘made in Israel’ is Cyberav3ngers legal target.”
The targeted PLCs are commonly used across multiple critical infrastructure sectors: water and wastewater systems, energy, food and beverage manufacturing, transportation systems, and healthcare [CISA Advisory AA23-335A]. Many devices were publicly exposed to the internet on default TCP port 20256 using default credentials.
Defensive Priority Actions:
Industrial control systems directly connected to the internet with default passwords represent critical risk. Organizations using Unitronics Vision Series PLCs should:
Change default passwords immediately (CISA Advisory AA23-335A provides specific guidance)
Remove ICS from direct internet exposure
Implement authentication logging and monitoring
Deploy network segmentation between IT and OT environments
Russia’s Heating System Attacks: A Preview of Wartime Capability
While China pre-positions quietly for potential future conflict, Russia has already demonstrated willingness to weaponize infrastructure attacks during active hostilities. The difference matters when assessing threat intent.
Sandworm Team, a threat group attributed to Russia’s GRU Unit 74455, deployed the FrostyGoop malware against Ukrainian municipal heating systems during winter 2022 [Mandiant]. The attack targeted a heating utility in Lviv, Ukraine, disrupting service to hundreds of apartment buildings in freezing conditions. The malware specifically targeted Modbus TCP communications used in industrial control systems, allowing attackers to manipulate heating equipment remotely.
This wasn’t a proof-of-concept. It was a weaponized cyberattack designed to cause civilian hardship during active conflict. The same threat group previously caused two separate blackouts in Ukraine (2015 and 2022) and was responsible for the 2017 NotPetya attack that spread globally, causing over $10 billion in damages to shipping companies, manufacturers, and hospitals worldwide.
The tactical pattern is clear: Russia has both the capability and documented willingness to manipulate physical infrastructure systems during geopolitical conflicts. The techniques used against Ukrainian heating systems would transfer directly to similar HVAC and building management systems across Western critical infrastructure. When we discuss “pre-positioning” by Chinese actors, Russia provides the case study for what that pre-positioning might be used for if conflicts escalate.
The Supply Chain Cascade Effect
The February 2024 Change Healthcare ransomware attack demonstrates how interconnected infrastructure creates cascading failures. Disclosed in October 2024, the breach affected 192.7 million individuals (increased from an initial 100 million estimate) and caused $2.457 billion in losses to parent company UnitedHealth Group [HHS Office for Civil Rights Breach Portal]. The root cause? A server without multifactor authentication.
The attack disrupted prescription processing systems nationwide, forced thousands of pharmacies to manual paper processing, and prevented patients from accessing medications for weeks [HIPAA Journal]. UnitedHealth Group established a Temporary Funding Assistance Program, paying around $8.5 billion in loans to help healthcare providers struggling financially during the outage.
This wasn’t a hospital being attacked. It was the payment processing infrastructure that thousands of healthcare providers depend on. As Oregon Senator Ron Wyden noted in his October 2024 letter to UnitedHealth leadership, “This hack could have been stopped with cybersecurity 101.”
The breach happened because a critical piece of infrastructure lacked basic security controls. The impact spread because healthcare is now a tightly coupled system where a single compromise can cascade across thousands of dependent organizations. When your local pharmacy can’t process prescriptions, it’s not because they got hacked. It’s because their payment processor got hacked. That’s the supply chain problem in critical infrastructure.
Supply Chain Risk Indicators:
Third-party vendors with remote access to operational networks
Shared authentication systems across multiple organizations
Payment processors or clearinghouses with system dependencies
Cloud service providers with broad customer access
From Nuisance to Physical Danger
The Canadian Centre for Cyber Security issued warnings in late 2024 about an escalating pattern: hacktivists increasingly targeting internet-exposed industrial control systems across critical infrastructure [Canadian Centre for Cyber Security]. These aren’t sophisticated nation-state campaigns. They’re opportunistic attacks exploiting poor security on publicly accessible systems. But the physical consequences are real.
Three Attacks, Three Escalating Threat Levels
Water Facility Pressure Manipulation (Canada): Hackers accessed a water treatment facility and tampered with water pressure valves, causing degraded service to the community. The attack didn’t contaminate water or cause emergency conditions, but it demonstrated direct manipulation of physical infrastructure serving civilian populations. Water pressure isn’t just a convenience metric. Insufficient pressure can prevent fire suppression systems from functioning properly and can allow contaminants to enter distribution systems through back-siphoning.
Oil and Gas False Alarm Attack: Attackers compromised an automated tank gauge (ATG) at a Canadian oil and gas facility, triggering false alarms. ATGs monitor liquid levels in storage tanks and trigger safety responses when thresholds are exceeded. These systems have been plagued by severe vulnerabilities for at least a decade, yet many remain internet-accessible with weak authentication. False alarms create operational disruption and, more dangerously, can lead to “alarm fatigue” where operators begin ignoring warnings. That’s when real emergencies get missed.
Agricultural Temperature Manipulation (Canadian Farm): The most concerning incident involved hackers manipulating temperature and humidity parameters in a grain-drying silo. The Canadian Centre for Cyber Security noted that the attackers’ actions could have resulted in unsafe conditions had they not been caught quickly. Grain silos operate within precise temperature and humidity ranges. Excessive moisture combined with heat creates conditions for spontaneous combustion. Grain dust explosions are among the most destructive industrial accidents, with blast pressures exceeding those of TNT. This wasn’t a theoretical risk. The hackers were manipulating parameters that could have caused an explosion.
The Internet-Exposed ICS Problem
There are at least 100,000 internet-exposed ICS devices worldwide, and they are in many cases easy to compromise [Canadian Centre for Cyber Security]. The types of vulnerable systems include:
Safety instrumented systems (SIS) that prevent hazardous conditions
Building management systems controlling HVAC, lighting, and physical security
Industrial IoT devices providing sensor data and control capabilities
Programmable logic controllers (PLCs) running automated processes
Human-machine interfaces (HMIs) that operators use to monitor and control systems
Remote terminal units (RTUs) that interface with SCADA systems in remote locations
Supervisory control and data acquisition (SCADA) systems managing entire facilities
The common thread: many of these systems were designed for isolated networks and later connected to the internet for remote monitoring and management. The connectivity came without corresponding security improvements.Nation-State Attribution and Strategic Intent
Threat Group Distribution
The distribution of the 167 tracked threat groups reveals strategic priorities across adversary nations:
China (55 groups): Playing the long game. Volt Typhoon represents PRC effort to pre-position in communications, energy, water, and transportation sectors [CISA Advisory AA24-038A]. These are lifeline infrastructure sectors supporting both civilian communities and military installations, with particular focus on Guam and U.S. Pacific territories. APT10 targets manufacturing intellectual property supporting China’s “Made in China 2025” industrial policy initiatives. APT41 infiltrates logistics companies to understand global supply chains. The pattern shows preparation for potential disruption during future geopolitical conflicts, not immediate financial gain.
Russia (24 groups): Proven willingness for physical damage. Sandworm Team (GRU Unit 74455) has caused real-world blackouts in Ukraine and deployed FrostyGoop malware against municipal heating systems during winter combat operations. The 2017 NotPetya attack, originally targeted at Ukraine, spread globally and caused over $10 billion in damages. Russia has demonstrated both capability and willingness to weaponize cyberattacks against physical infrastructure during active conflicts.
Iran (12 groups): Infrastructure as political messaging. CyberAv3ngers, affiliated with IRGC Cyber-Electronic Command, specifically targets water treatment facilities, power substations, and natural gas systems with explicit pro-Palestinian messaging [U.S. Treasury OFAC]. They publicly deface control system interfaces while demonstrating restraint to avoid triggering military responses. Iran uses infrastructure attacks as low-intensity warfare and political signaling.
North Korea (6 groups): Follow the money. Kimsuky and related groups target critical infrastructure primarily for financial theft to fund the regime and evade sanctions. They target financial systems, defense contractors, and manufacturing to steal money and gather intelligence that can be sold or used for bargaining leverage.
Actionable Defensive Framework
1. Network Segmentation Between IT and OT
Most breaches start in corporate IT networks (email, file servers, business systems) and then pivot to operational technology (factory floor, water treatment controls, power distribution). The IT/OT convergence that’s happened over the past decade as organizations connected previously isolated industrial systems to corporate networks has created these pivot opportunities.
Critical implementation: Industrial control systems should not be accessible from corporate email networks. Period. Use dedicated jump boxes that create controlled transition points with strict monitoring. An engineer shouldn’t be able to check email and access SCADA systems from the same workstation without explicit authentication and logging at the boundary.
2. Vendor Access as an Attack Vector
When Black Basta compromises a manufacturing company’s IT support provider, they inherit access to all that provider’s clients. Third-party remote access is one of the most exploited vectors in critical infrastructure compromise.
Required controls: Multifactor authentication for ALL vendor access, no exceptions. Log every remote session with timestamp and activity details. Conduct quarterly vendor access reviews to remove accounts for contractors who changed roles, left companies, or no longer need access. Many breaches happen through vendor accounts that should have been disabled months earlier.
3. Assume Breach, Focus on Detection
If Volt Typhoon can maintain access for five years before detection, prevention-only strategies have failed. Organizations need to hunt for threats assuming attackers are already inside.
Behavioral monitoring priorities:
Engineering workstations communicating with unusual cloud services or external IPs
Off-hours access to SCADA systems, especially on weekends or holidays
Unusual parameter changes to industrial processes (flow rates, chemical dosing, pressure settings)
Lateral movement between IT and OT networks, particularly from accounts that shouldn’t cross that boundary
These behavioral indicators matter more than signature-based detection when attackers are using legitimate tools and valid credentials.
4. Social Engineering Training That Actually Works
Stop sending employees fake phishing tests with “gotcha” penalties that breed resentment. Instead, teach them the actual attack methods adversaries are using right now:
QR code scams and Microsoft Teams impersonation (show them the Black Basta technique)
Email bombing combined with fake IT support
Fake job posting malware delivery (particularly effective against engineers recruited via LinkedIn)
Out-of-band verification procedures for urgent requests (always call back using a known number)
Make the training contextual and relevant. Use real examples from recent attacks. Explain why these techniques work psychologically so employees understand the manipulation, not just the technical mechanics.
The Bottom Line
The threat landscape analyzed here isn’t abstract cyber risk. It’s the early phase of geopolitical competition where critical infrastructure serves as contested terrain. Nation-states are pre-positioning for future conflicts. Criminal groups target industrial processes, not just data. Social engineering bypasses technical security. Supply chain dependencies create cascading failures.
For executives and boards: ICS security is enterprise risk management requiring board-level attention, budget, and accountability. It’s not just an IT problem. When adversaries can manipulate water treatment or power distribution, you’re dealing with operational risk, regulatory risk, reputational risk, and potential physical safety risk.
For technical teams: Adversaries are patient, well-resourced, and likely already inside many networks. Defense requires assuming breach, detecting behavioral anomalies, and having incident response plans that account for physical system manipulation, not just data theft. Your IR plan probably covers ransomware. Does it cover someone manipulating industrial process parameters?
For policy makers: Current compliance frameworks are insufficient. The threat has evolved from espionage to sabotage, and security requirements must match that reality. Passing annual audits doesn’t mean your water treatment plant can’t be compromised through an internet-connected PLC with a default password.
Research Sources:
Intruvent BRACE CTI Platform
CISA Advisories: AA24-038A (Volt Typhoon), AA23-335A (CyberAv3ngers)
Microsoft Security Blog: Volt Typhoon Campaign Analysis
The Record: NSA Assessment on Volt Typhoon Disruption
ReliaQuest Threat Research: Black Basta Social Engineering Evolution
U.S. Treasury OFAC: Iranian IRGC-CEC Sanctions
HHS Office for Civil Rights: Change Healthcare Breach Portal Data
DefenseScoop: Air Force Cyber Leadership Assessment
HIPAA Journal: 2024 Healthcare Ransomware Analysis
NSA, FBI Joint Cybersecurity Advisories
Analysis current as of October 31, 2025. Intelligence derived from BRACE CTI analysis, CISA advisories, threat vendor reporting, and open-source intelligence.



The data showing 49% of threat reports targeting ICS/SCADA systems is genuinely alarming. The shift from espionge to pre-positioning for physical disruption represents a qualititive change in the threat landscpe. The Volt Typhoon five-year persistence example really underscores why behavioral anomaly detection is so critical now, you cant just rely on perimeter defenses anymore.
Admittedly our intel agents skew a bit toward Critical infrastructure. But still, I was shocked at the number of reports showing ICS/SCADA targeting. Especially because it meant that that type of activity was far more prevalent than the financial actors/attacks that we generally see. Thanks for the great comment!