Intruvent EDGE: Cyber Threat Roundup
Salt Typhoon remains embedded in nine US telecoms with no proof of eradication. Volt Typhoon has pre-positioned in 10 critical infrastructure sectors. What's their end game?
Welcome to the first edition of The Intruvent Edge for 2026. This month, we’re unpacking what December 2025 revealed about the threats that will define the year ahead.
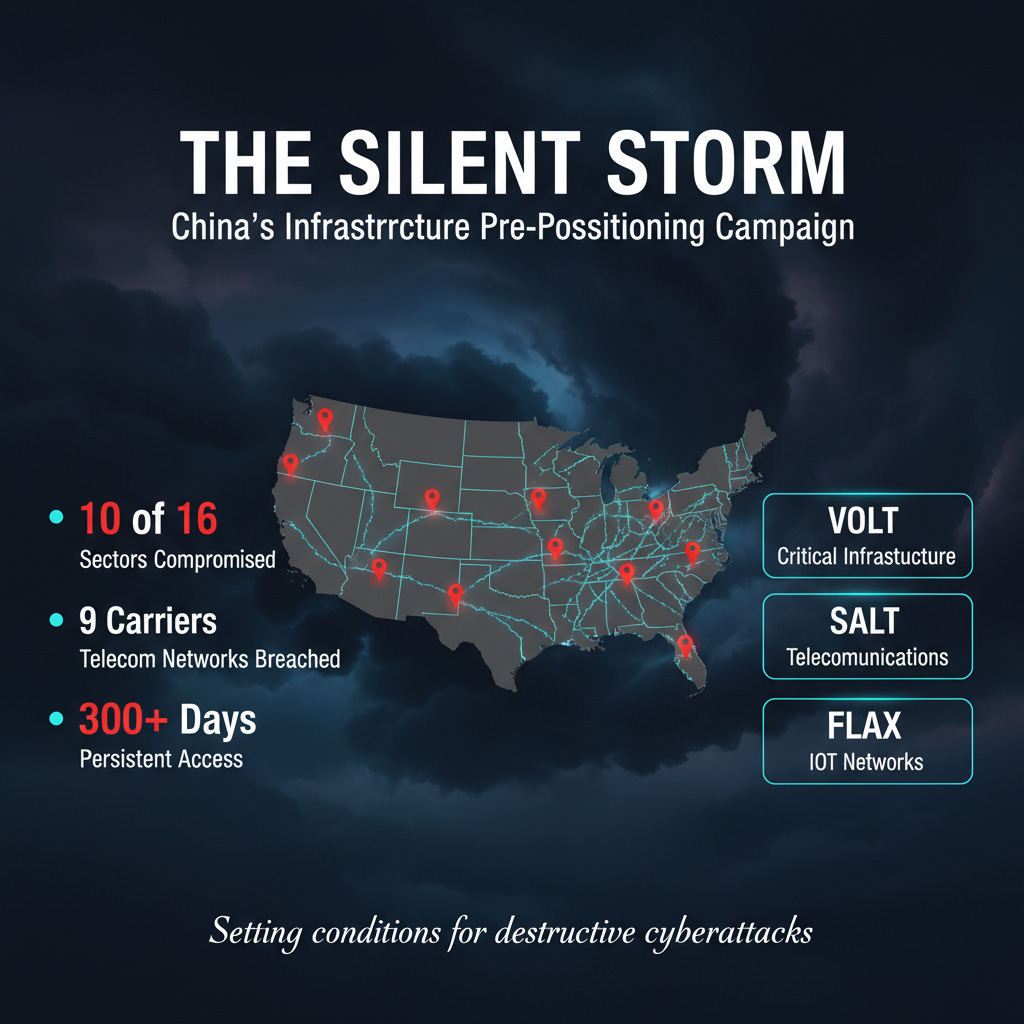
The Silent Invasion is No Longer Silent
There’s a storm brewing in America’s digital infrastructure, and it has a name: Typhoon.
Not one storm, but a family of them. Volt Typhoon. Salt Typhoon. Flax Typhoon. These are Microsoft’s designations for what intelligence officials are now calling the most sophisticated pre-positioning campaign in cyber history. As 2025 drew to a close, the scope of that campaign became clear.
The numbers don’t lie:
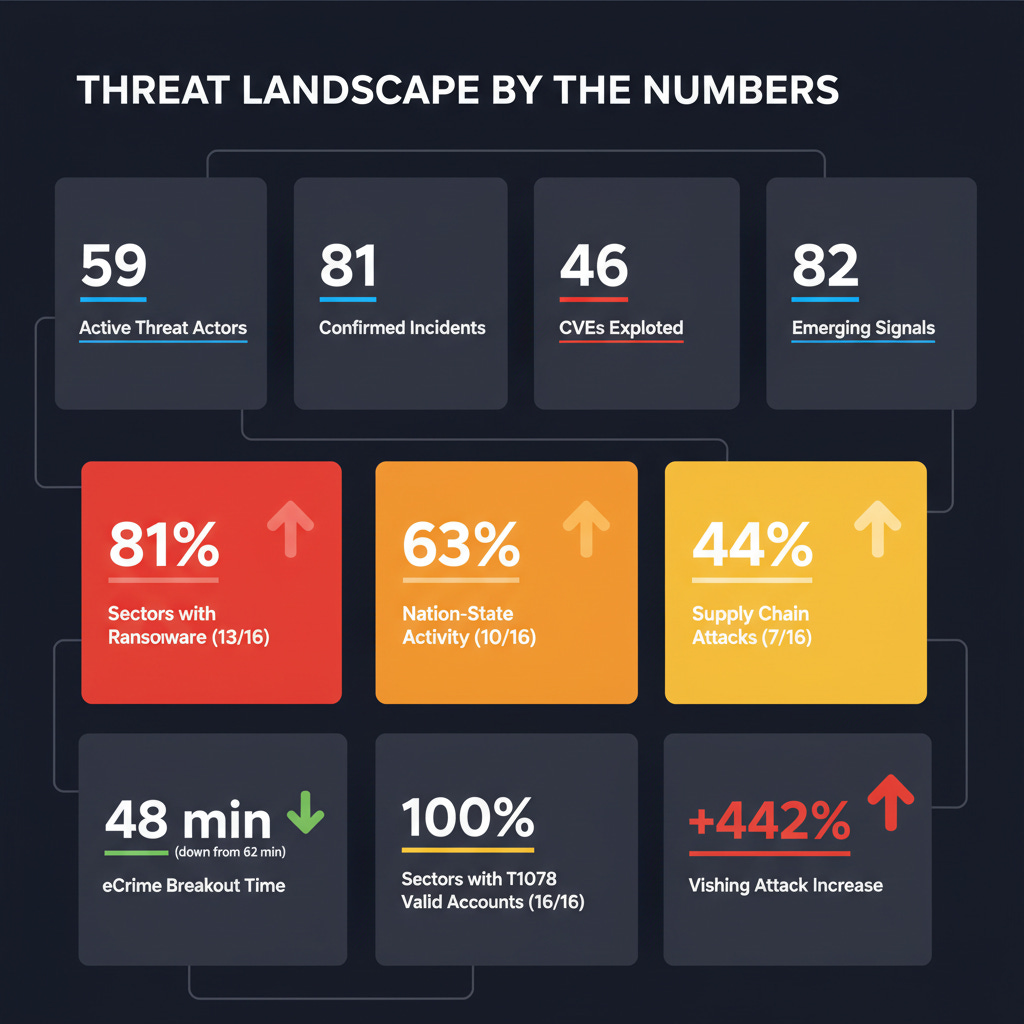
Our December 2025 Cross-Sector Threat Intelligence analysis tracked 59 active threat actors across 16 critical infrastructure sectors, with 81 confirmed incidents and 46 actively exploited CVEs (Common Vulnerabilities and Exposures). But behind those statistics lies a story that should keep every security professional awake at night.
Volt Typhoon, the Chinese state-sponsored group nicknamed “The Silent Storm,” has now pre-positioned itself in 10 of 16 critical infrastructure sectors. That’s not a typo. Not 10 companies. Not 10 networks. Ten entire sectors of American critical infrastructure now have Chinese operatives quietly waiting, watching, and preparing.
As one Air Force cyber leader put it in September: “They haven’t done anything with it. Why? Because they’re probably setting the conditions to execute destructive cyberattacks, should there be a regional conflict in the Pacific over Taiwan.”
Last week news broke that Salt Typhoon, Volt Typhoon’s espionage-focused cousin, had breached Congressional committee staff emails. The Intelligence Committee. Foreign Affairs. Armed Services. China. The hackers weren’t just reading government communications; they were accessing the very committees tasked with confronting Chinese aggression.
The fundamental question facing defenders in 2026: will we be ready when dormant access becomes active attack?
At Intruvent, we’d like to help. If you work in cybersecurity, you can grab our Threat Actor Profiles (TAPs) and Threat Hunting Guides from our Threat Intel hub here. If you’d like a more detailed analysis into cross sector trends, grab our December cross-sector report here.
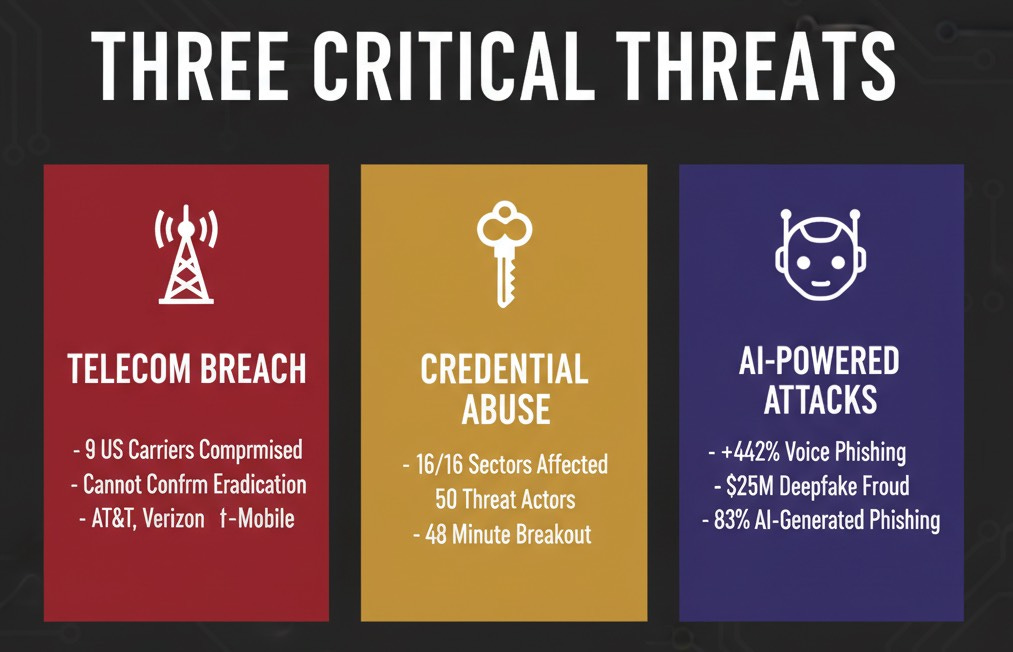
Three Things Every Security Leader Needs to Know Right Now
1. Salt Typhoon: The Breach That Won’t End
If there’s one threat that defined December 2025, it’s the uncomfortable reality that Salt Typhoon, the Chinese state-sponsored group haunting American telecommunications, isn’t going anywhere.
Senate Commerce Committee experts delivered a stark verdict last month: nine major US telecommunications carriers, including Verizon, AT&T, and T-Mobile, have failed to prove Chinese hackers have been eradicated from their networks. Not “might still be compromised.” Cannot prove eradication.
Why Salt Typhoon matters:
This isn’t a failure of detection, it’s a demonstration of capability. Salt Typhoon has maintained access through multiple detection attempts, credential rotations, and infrastructure changes. They’re proving they can stay as long as they want.
The implications extend far beyond wiretapping. Telecom infrastructure carries more than calls. Authentication systems, SMS-based MFA, and carrier-trusted certificates all flow through networks that remain compromised. If your organization relies on telecom-based security controls: SMS codes, carrier-verified identity, or any trust assumptions rooted in phone networks…it’s time to reassess.
The scope is staggering: Intelligence collection continues with potential for future disruption. And the attackers aren’t just listening. They’re positioned to act when the strategic moment arrives.
2. Valid Accounts Are the Universal Skeleton Key
Here’s the most sobering finding from our December analysis: T1078 (Valid Accounts) appeared in ALL 16 critical infrastructure sectors, with 50 different threat actors leveraging credential-based access.
This is the dominant technique across the board.
Whether it’s Volt Typhoon maintaining years-long persistence through legitimate credentials, ransomware affiliates using MFA bombing and SIM swapping, or Salt Typhoon accessing telecoms through unpatched VPNs with weak passwords, the message is clear. Attackers don’t need to break down doors when they have keys.
The 48-minute average eCrime breakout time we tracked in December (down from 62 minutes in 2024) means defenders have less than an hour from initial compromise to widespread lateral movement. If your credential hygiene isn’t excellent, that window is functionally zero.
3. The AI Arms Race Has Arrived
The 442% increase in voice phishing (vishing) attacks between the first and second half of 2024 wasn’t an anomaly. It was a preview.
In early 2025, a European energy conglomerate lost $25 million when attackers used a deepfake audio clone of the CFO to authorize a wire transfer. The voice sounded perfect: pauses, tone, cadence. By the time anyone realized what happened, the money was gone.
Deepfake-as-a-Service (DaaS) platforms became widely accessible in 2025, putting sophisticated voice cloning within reach of criminals at every skill level. Groups like UNC6040, BlackBasta, and even the Lazarus Group are now weaving synthetic audio into their core playbooks.
The readiness gap is real. Only 34% of organizations in targeted industries report feeling prepared for deepfake-enabled attacks. Meanwhile, nearly 83% of phishing emails are now AI-generated, making traditional detection methods increasingly obsolete.
The Good News (Yes, There Is Some)
Amid the escalating threats, December revealed genuine progress in the defender’s arsenal:
Healthcare is learning to say no. Ransom payments in the healthcare sector plummeted 91%, from $4 million average demands in 2024 to just $343,000 in 2025. Actual payments dropped even more dramatically, from $1.47 million to $150,000. Nearly 60% of healthcare providers now recover within one week of an attack, up from just 21% the previous year.
Encryption attacks are being stopped. For the first time in three years, the percentage of ransomware attacks successfully encrypting healthcare data dropped to 34%, less than half the 74% reported in 2024. Defenders are catching attacks earlier and stopping them before the payload deploys.
Global coordination is working. The disruption of LockBit infrastructure, the sanctioning of companies supporting Salt Typhoon, and the takedown of multiple ransomware operations demonstrate that international cooperation can meaningfully impact criminal ecosystems.
Resilience is possible. But it requires investment, vigilance, and a willingness to implement the fundamentals consistently.
The Threat Landscape by the Numbers
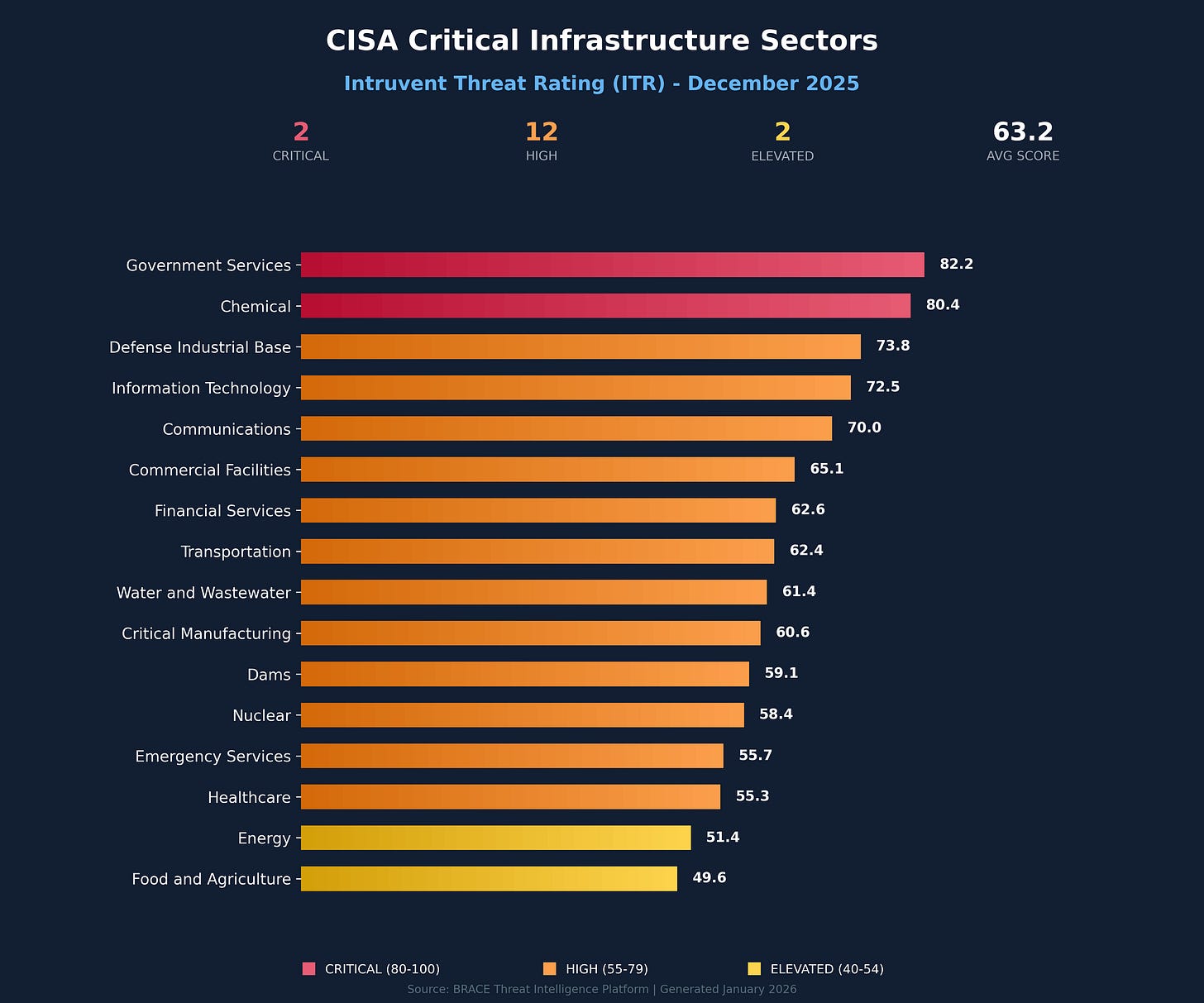
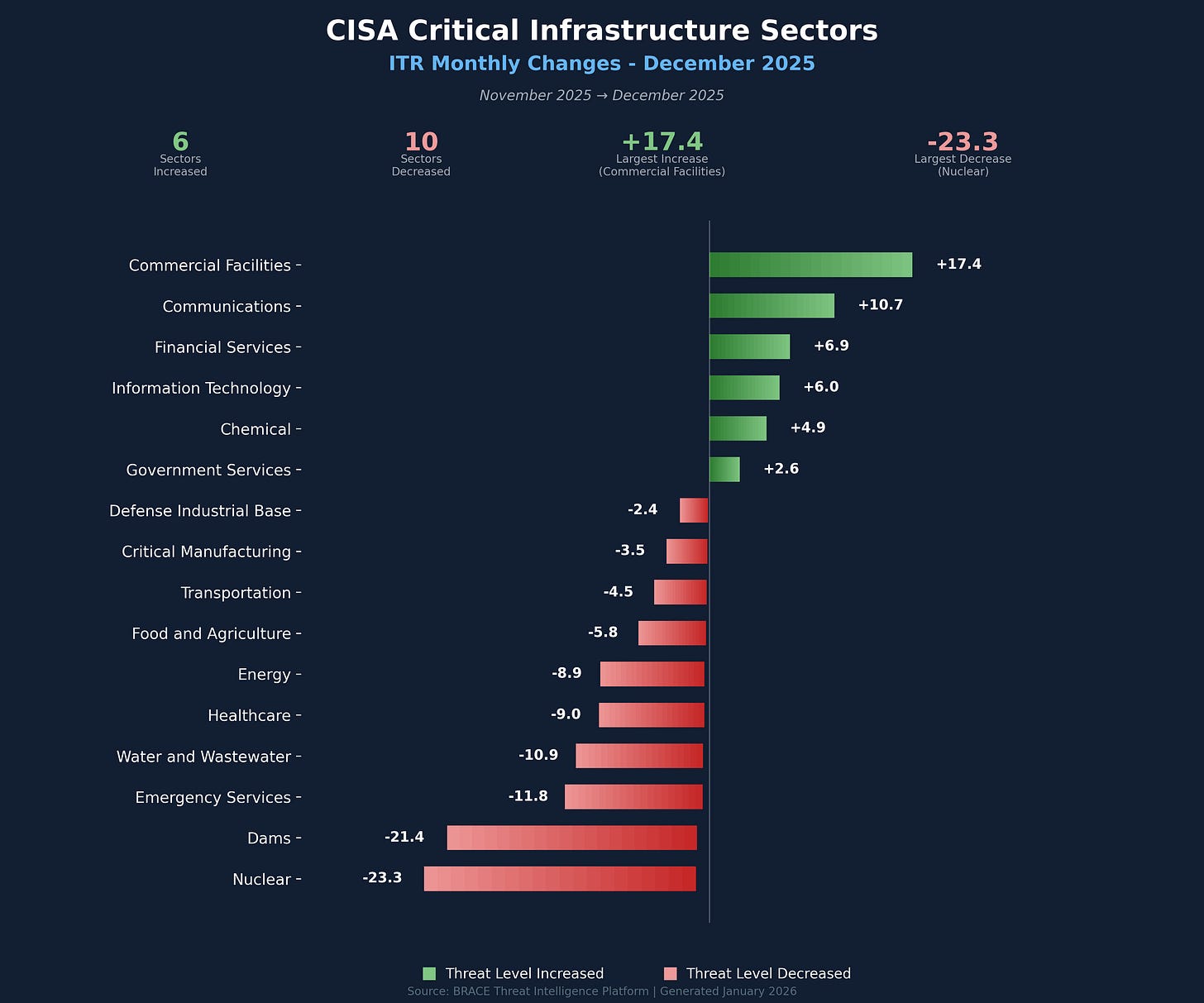
Critical Infrastructure Sectors by Intruvent Threat Rating
Our proprietary Intruvent Threat Rating aggregates threat actor pressure, vulnerability exposure, attack success rates, and sophistication metrics into a single risk score:
The 36% surge in Commercial Facilities risk stands out this month, reflecting expanded ransomware targeting of retail, hospitality, and entertainment venues. Communications sector risk also climbed 18%, driven by the ongoing Salt Typhoon telecom compromises and growing recognition that technology supply chains represent critical attack surfaces for nation-state actors.
Emerging Signals: What to Watch in 2026
Supply Chain Cascade Risk
87% of December healthcare incidents originated from vendor or supplier compromise. The Oracle Cloud breach affected 140,000+ tenants. Supply chain attacks have become the preferred attack vector for maximizing impact.
OT/ICS Exposure Acceleration
Dragos reports a 40% rise in internet-exposed industrial control systems. With Volt Typhoon pre-positioned in energy, water, and transportation infrastructure, the convergence of IT and OT security has moved from theoretical concern to existential imperative. A SANS Institute 2025 survey found only 14% of organizations feel “fully prepared” for emerging OT threats.
AI/ML Infrastructure as Target
Trend Micro researchers documented increased reconnaissance of cloud ML platforms. Expect GPU cluster cryptojacking and ML pipeline supply chain attacks to emerge as threat actors realize the value (and vulnerability) of AI training infrastructure.
Insurance-Calibrated Ransomware
The Interlock ransomware group was observed stealing cyber insurance policies during intrusions to set demands precisely below coverage limits. This level of sophistication suggests ransomware operators are treating attacks as business negotiations, not smash-and-grab operations.
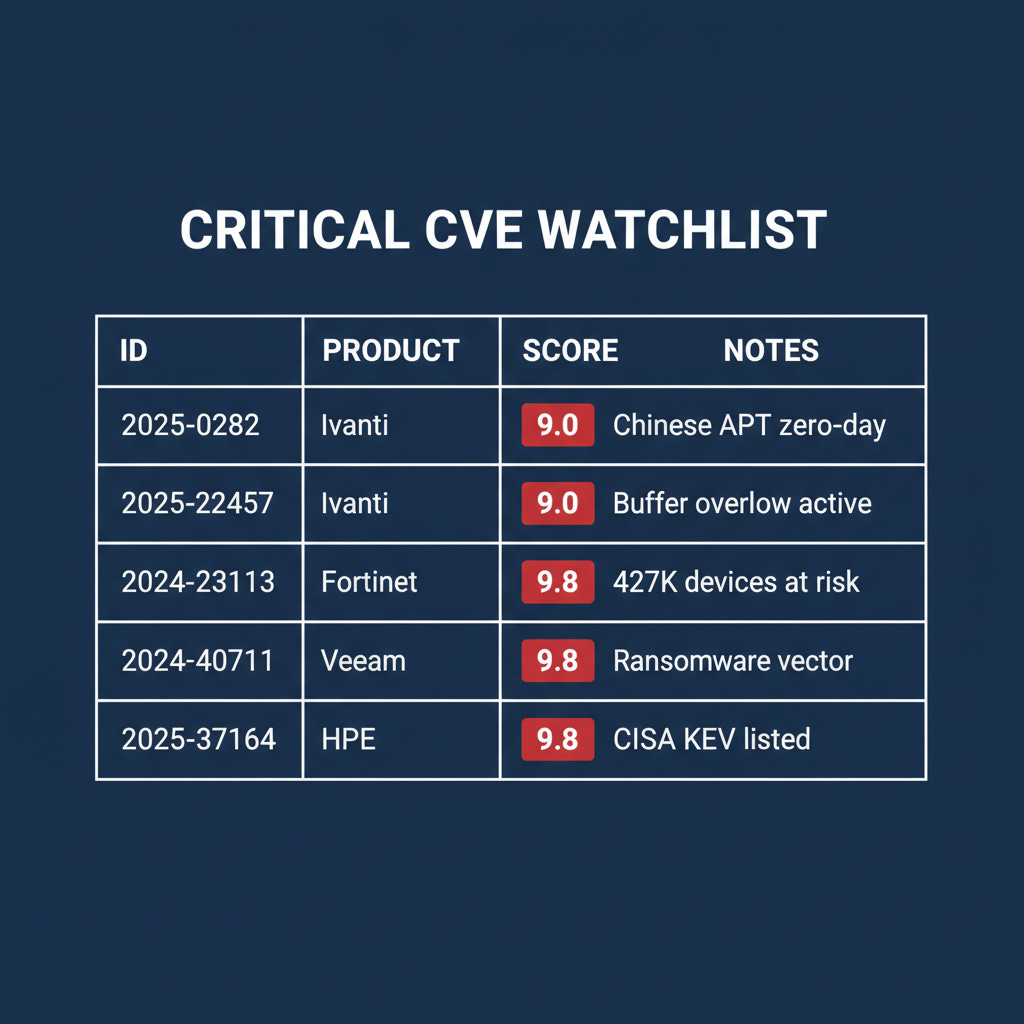
Critical Patch Priorities for January 2026
Before we dive into the action checklist, let’s be specific about the vulnerabilities demanding immediate attention. These are being actively exploited right now:
Why these specifically? Each of these vulnerabilities sits at the intersection of three factors: confirmed active exploitation, presence in enterprise perimeter infrastructure (VPNs, firewalls, backup systems), and use by the threat actors we’re tracking—both nation-state APTs and ransomware operators.
Your January 2026 Action Checklist
This Week:
Verify MFA is enabled on all VPN solutions (SonicWall, Ivanti, Fortinet priority)
CRITICAL: Patch Ivanti Connect Secure (CVE-2025-0282, CVE-2025-22457). Active nation-state exploitation by Chinese APT UNC5221.
Patch Fortinet FortiOS/FortiProxy (CVE-2024-23113, CVSS 9.8). Over 427K devices exposed; active ransomware vector.
Patch Veeam Backup & Replication (CVE-2024-40711). Akira and Fog ransomware actively exploiting.
Audit third-party and vendor access credentials
This Month:
Review and test OT/IT network segmentation
Conduct backup restoration drill (not just backup verification)
Implement out-of-band verification protocols for financial requests
Brief executive team on deepfake vishing risks and establish code word procedures
This Quarter:
Deploy behavioral detection for T1078 (Valid Accounts) across all environments
Assess supply chain vendor security postures
Develop incident response playbooks for ransomware + data extortion scenarios
The Bottom Line
2025 ended with a stark reminder: the most dangerous cyber operations are often the ones you can’t see. Volt Typhoon has spent years quietly mapping American infrastructure. Salt Typhoon continues to dwell in telecom networks despite months of supposed remediation. The ransomware ecosystem continues to mature, with operators treating attacks as calculated business negotiations rather than opportunistic smash-and-grabs.
But the defender’s toolkit is evolving too. Lower ransom payments, faster recovery times, and increased international cooperation show that resilience is achievable for organizations willing to invest in fundamentals: credential security, network segmentation, tested backups, and verified response procedures.
The threats of 2026 won’t be subtle or merciful. But they won’t be invincible either.
Stay vigilant. Stay prepared. And stay tuned.
Have questions about the threats discussed in this newsletter? Need sector-specific guidance for your organization? Contact the Intruvent team at contact@intruvent.com or explore our BRACE Threat Intelligence platform at www.intruvent.com/brace.
About This Report
This newsletter synthesizes findings from BRACE Cross-Sector Threat Intelligence (December 2025), supplemented by research from CrowdStrike, Sophos, Microsoft, CISA, Dragos, and open-source threat intelligence. All sector statistics sourced from BRACE Threat Intelligence Platform unless otherwise noted.
The Intruvent Edge is published every other week. Prevent This is published every week. Subscribe at intruvent.com/edge